Network scanning tools are essential for maintaining security, optimizing performance, and troubleshooting network issues. Whether you’re a seasoned IT professional or a small business owner, understanding the capabilities and benefits of these tools is crucial in today’s interconnected world. Selecting the right network scanning tool can significantly impact your ability to identify vulnerabilities and maintain a robust network infrastructure. We will delve into the world of top network scanning tools, exploring their features, benefits, and use cases.
Choosing the right network scanning tool depends on your specific needs and the scale of your network. Some tools excel at vulnerability scanning while others are better suited for network mapping and inventory management. Knowing the differences can save you time and resources.
A key feature of effective network scanning tools is their ability to identify and classify connected devices. This allows administrators to maintain an accurate inventory of hardware and software, facilitating better resource management and security control. Let’s examine some of the key aspects of these powerful tools. This knowledge will equip you to choose the solution best suited for your networking needs.
Understanding Network Scanning Tools: Types and Features
Network scanning tools are categorized based on their functionality and scanning techniques. Some common types include:
- Port Scanners: These tools identify open ports on a network device, helping pinpoint potential security vulnerabilities.
- Vulnerability Scanners: These tools go beyond port scanning by actively probing for known vulnerabilities in software and operating systems. Check out our resource on vulnerability scanning open source tool.
- Network Mappers: These tools create visual representations of network topology, making it easier to understand network structure and identify devices.
- IP Scanners: These tools specifically scan for IP addresses on a network, useful for identifying connected devices and potential rogue devices. For those interested in IP phone scanning, we have a dedicated guide on tool to scan network for ip phones.
Several key features differentiate network scanning tools:
- Scanning Speed: The speed at which a tool can scan a network impacts the efficiency of network administration.
- Reporting Capabilities: Clear and concise reports are crucial for understanding scan results and identifying vulnerabilities.
- Customization: The ability to customize scans based on specific needs allows for targeted analysis and efficient resource utilization.
- Integration with other tools: Seamless integration with other security and network management tools enhances overall network security posture.
 Network Scanning Tool Types – Port Scanner, Vulnerability Scanner, Network Mapper, IP Scanner
Network Scanning Tool Types – Port Scanner, Vulnerability Scanner, Network Mapper, IP Scanner
Choosing the Right Tool for Your Needs
Choosing the right network scanning tool is crucial for effective network management. Considerations include:
- Network Size: Larger networks require tools that can handle high volumes of data and scan quickly.
- Security Requirements: Organizations with stringent security needs should prioritize vulnerability scanners with comprehensive databases of known threats. Tools that can scan for personal data may also be relevant. You can explore more about this topic at software tools for scanning for personal data.
- Budget: Free and open-source tools are available, but commercial solutions often offer advanced features and support.
- Technical Expertise: Some tools are designed for experienced IT professionals while others offer user-friendly interfaces for less technical users.
Top Network Scanning Tools in the Market
Several top network scanning tools cater to diverse needs. Some popular choices include:
- Nmap: A powerful and versatile open-source tool widely used for port scanning, network mapping, and OS detection.
- Nessus Essentials: A free vulnerability scanner ideal for home users and small businesses looking for basic vulnerability assessment.
- Wireshark: A powerful network protocol analyzer that captures and analyzes network traffic, invaluable for troubleshooting network issues. If you’re interested in auto scanning tools, check out our article on auto scanning tool with laptop.
- SolarWinds Network Performance Monitor: A comprehensive commercial tool offering advanced network monitoring and performance analysis capabilities.
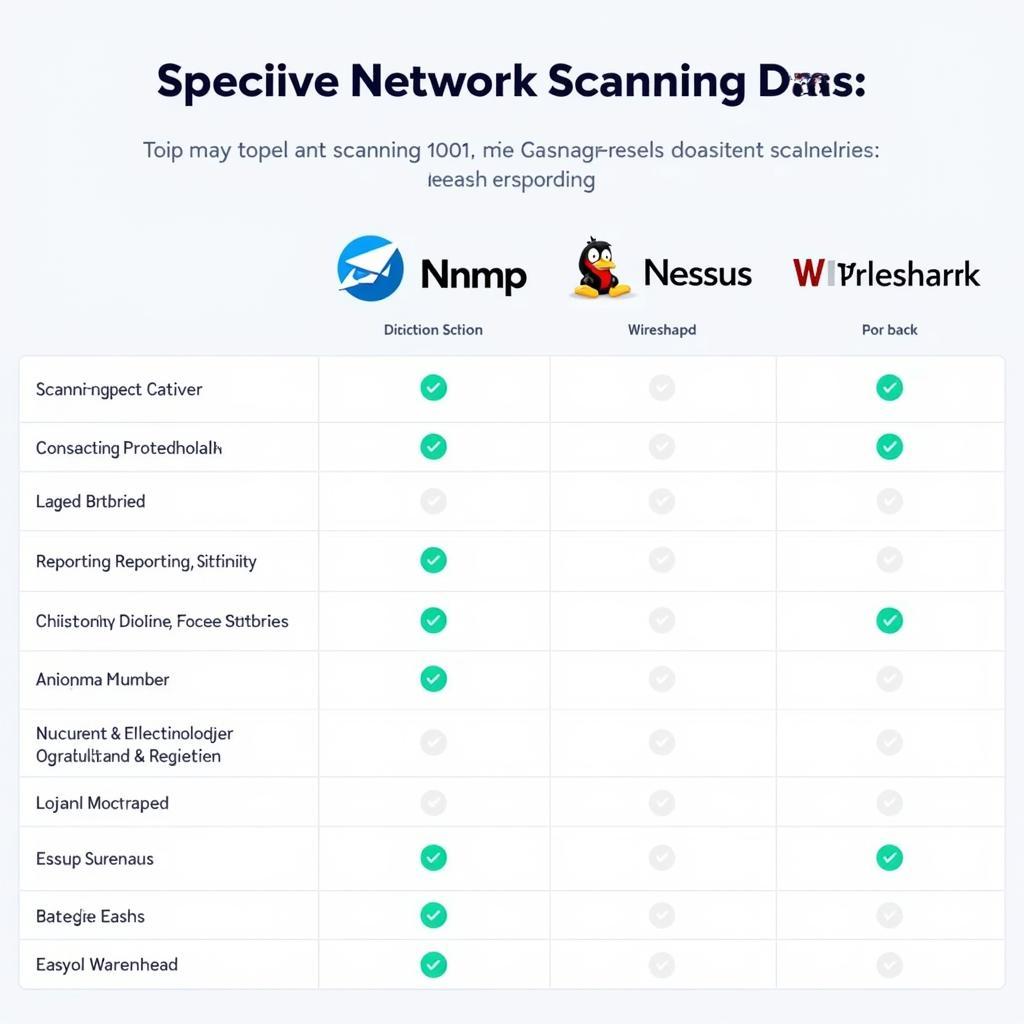 Top Network Scanning Tools Comparison Chart
Top Network Scanning Tools Comparison Chart
How to Use Network Scanning Tools Effectively
Maximizing the effectiveness of network scanning tools involves several key practices:
- Regular Scanning: Scheduled scans ensure ongoing network security and performance monitoring.
- Analyzing Scan Results: Careful analysis of scan reports is essential for identifying and addressing potential vulnerabilities. Perhaps you’re looking to scan your hard disk; you can find useful resources on hard disk scan tools.
- Staying Updated: Keeping software and vulnerability databases up-to-date ensures accurate and relevant scan results.
“Regularly updating your network scanning tools and vulnerability databases is like changing the locks on your doors – it keeps the bad actors out.” – John Smith, Senior Network Security Analyst
“Understanding your network’s topology is half the battle. Network mapping tools provide the visual clarity needed to effectively manage and secure your network infrastructure.” – Maria Garcia, Network Architect
 Effective Network Scanning Strategies – Regular Scanning, Analyzing Scan Results, Staying Updated
Effective Network Scanning Strategies – Regular Scanning, Analyzing Scan Results, Staying Updated
Conclusion
Top network scanning tools play a vital role in maintaining a secure and efficient network. Choosing the right tool and utilizing it effectively empowers you to identify vulnerabilities, troubleshoot problems, and optimize network performance. By investing in robust network scanning tools, you contribute significantly to the overall health and security of your network infrastructure.
FAQ
-
What is a port scan?
A port scan checks for open ports on a network device. -
Why is vulnerability scanning important?
Vulnerability scanning helps identify weaknesses in software and systems that could be exploited by attackers. -
What are the benefits of network mapping?
Network mapping provides a visual representation of network structure, facilitating better understanding and management. -
Are free network scanning tools effective?
Free tools can be effective for basic scanning, but commercial solutions often provide advanced features. -
How often should I scan my network?
Regular scans, ideally weekly or monthly, are recommended. -
What is a rogue device?
A rogue device is an unauthorized device connected to the network. -
How can I improve my network security?
Using network scanning tools, firewalls, and intrusion detection systems can enhance network security.
Need further assistance? Contact us via WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. We have a 24/7 customer support team. We also have other resources available on our website addressing related topics that may interest you.


