Website security is paramount in today’s digital landscape. Using the right tools for scanning website vulnerabilities can protect your site from cyber threats and ensure a safe browsing experience for your users. Understanding the various vulnerabilities and employing appropriate scanning tools is crucial for maintaining a robust online presence.
Why Website Vulnerability Scanning is Crucial
Regular vulnerability scanning helps identify weaknesses in your website’s security before attackers can exploit them. These weaknesses can range from cross-site scripting (XSS) and SQL injection to outdated software and insecure server configurations. Ignoring these vulnerabilities can lead to data breaches, reputational damage, and financial losses.
A proactive approach to website security involves regular scanning, prompt patching, and continuous monitoring. This not only safeguards your data and users but also strengthens your brand’s credibility and trust. Early detection of vulnerabilities allows you to address them before they become major issues, saving you valuable time and resources in the long run.
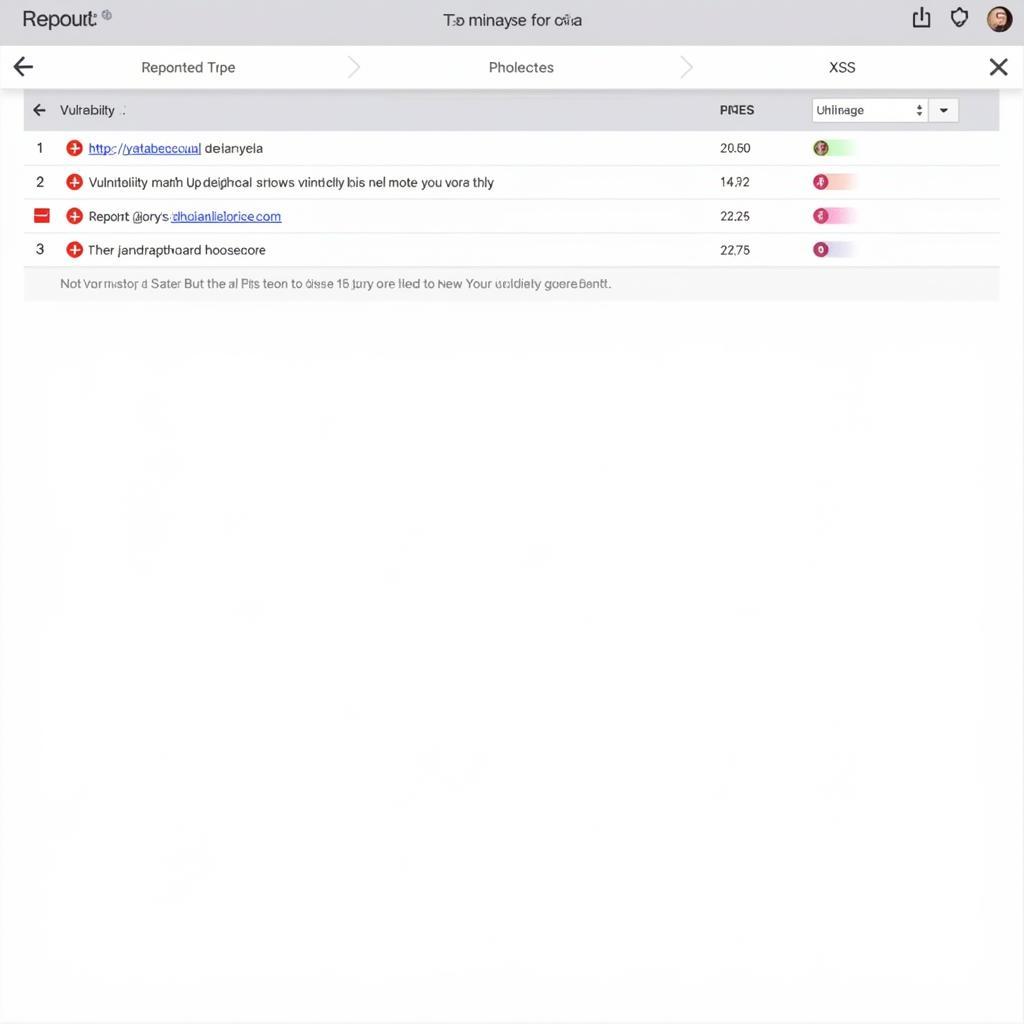 Website Vulnerability Scan Report Showing Critical Vulnerabilities
Website Vulnerability Scan Report Showing Critical Vulnerabilities
Categories of Website Vulnerability Scanners
Website vulnerability scanners are categorized based on their functionalities and target vulnerabilities. Understanding these categories helps you choose the right tool for your specific needs.
Network-Based Scanners
These tools scan your website’s network infrastructure for open ports, misconfigurations, and vulnerabilities in network devices like routers and firewalls.
Web Application Scanners
These scanners specifically target vulnerabilities within web applications, such as cross-site scripting (XSS), SQL injection, and insecure authentication mechanisms. You can find some good web server security scan tools listed on our site.
Database Scanners
These tools focus on identifying vulnerabilities within databases, ensuring data integrity and preventing unauthorized access. They check for weak passwords, insecure configurations, and potential SQL injection vulnerabilities.
WordPress Scanners
Designed specifically for WordPress websites, these scanners identify vulnerabilities in plugins, themes, and core files, offering tailored security solutions.
Key Features of Effective Tools for Scanning Website Vulnerabilities
Choosing the right vulnerability scanner requires careful consideration of essential features. A comprehensive tool should offer:
- Automated Scanning: Regular automated scans save time and ensure consistent security checks.
- Comprehensive Vulnerability Coverage: The tool should detect a wide range of vulnerabilities, including common and emerging threats. Check out our page on cve scanning tool for more information.
- Detailed Reporting: Clear and concise reports with actionable recommendations are crucial for effective remediation.
- Integration with other security tools: Seamless integration with other security tools streamlines the vulnerability management process.
How to Use a Website Vulnerability Scanner
Using a website vulnerability scanner typically involves these steps:
- Select a suitable scanner: Choose a tool that meets your specific needs and budget. Some helpful free pci scanning tool options are available.
- Configure the scan: Specify the target website, scanning depth, and vulnerability types.
- Initiate the scan: Start the scanning process.
- Analyze the report: Review the scan results and identify vulnerabilities. Tools for scanning for personal data are also available; check out our software tools for scanning for personal data page.
- Remediate vulnerabilities: Implement necessary fixes to address the identified weaknesses.
- Repeat the scan: Regularly rescan to ensure ongoing security. Consider using a container scanning tool for enhanced security in containerized environments.
“Regular vulnerability scanning is not just a best practice; it’s a necessity. It’s like getting regular checkups for your website’s health,” says John Smith, Cybersecurity Expert at SecureTech Solutions.
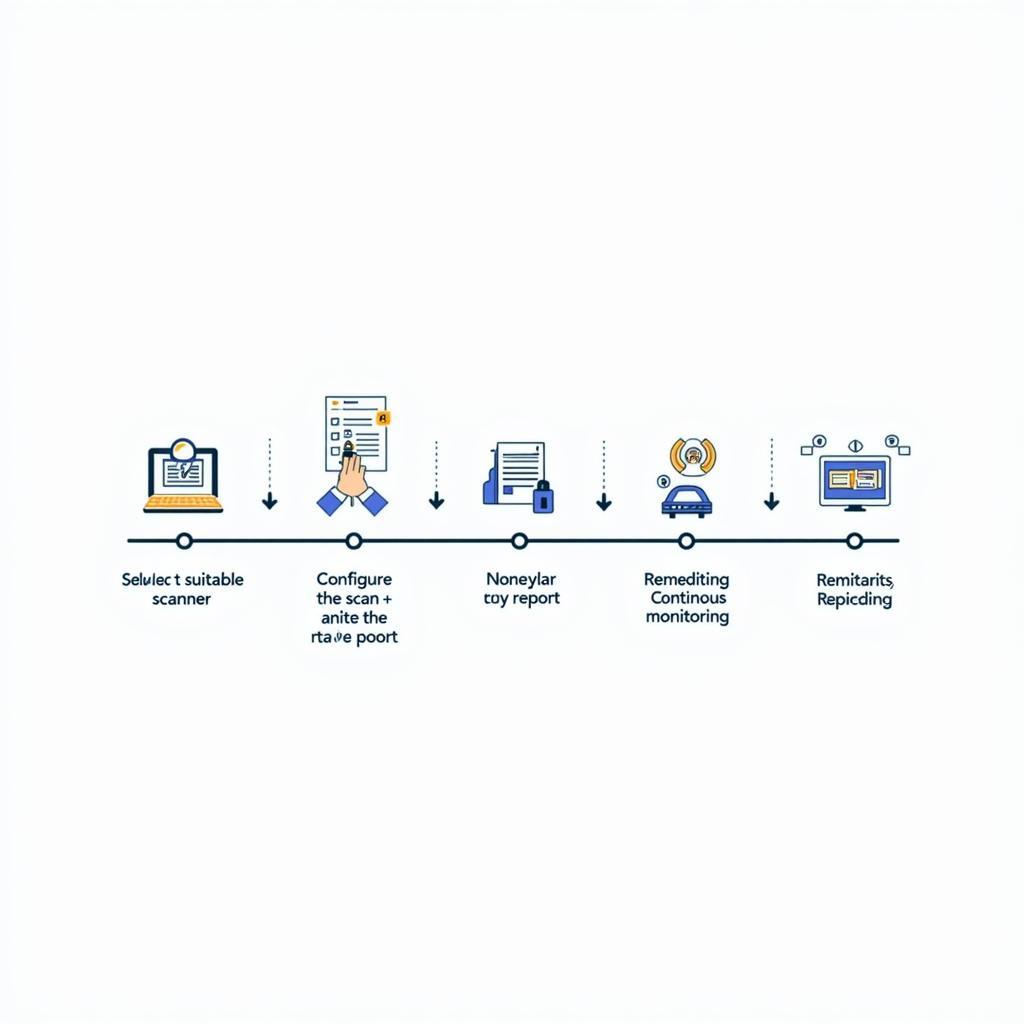 Steps to Use a Website Vulnerability Scanner Effectively
Steps to Use a Website Vulnerability Scanner Effectively
Conclusion
Utilizing effective tools for scanning website vulnerabilities is crucial for maintaining a secure online presence. By understanding the various types of vulnerabilities and implementing regular scanning practices, you can protect your website, data, and users from cyber threats. Regular scanning, prompt remediation, and continuous monitoring are essential for robust website security.
FAQ
- What are the most common website vulnerabilities?
- How often should I scan my website for vulnerabilities?
- What is the difference between a vulnerability scan and a penetration test?
- How much does a website vulnerability scanner cost?
- Can I scan my website for vulnerabilities for free?
- How do I fix vulnerabilities found by a scanner?
- What are the benefits of using a cloud-based vulnerability scanner?
Common Website Vulnerability Scenarios
- Scenario 1: A small business website experiences a data breach due to an SQL injection vulnerability.
- Scenario 2: An e-commerce website loses customer trust after a cross-site scripting attack.
- Scenario 3: A government website is defaced due to an outdated software vulnerability.
Further Reading and Resources
- Website Security Best Practices
- Common Web Application Vulnerabilities
- Choosing the Right Vulnerability Scanner
Need assistance? Contact us via WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. Our customer service team is available 24/7.


