Imagine this: you’re a mechanic in a bustling Detroit garage, specializing in European cars. You’ve got a brand new Audi A8 on the lift, a technological marvel with more sensors and ECUs than you can count. Suddenly, the check engine light flashes. Your first instinct? Grab your trusty dealer scanner, the ultimate tool for understanding what’s happening under the hood.
Just like that scanner reveals hidden issues in a car’s electrical system, port scanning tools are essential for diagnosing vulnerabilities in your network. They provide a window into your digital infrastructure, identifying open ports and potential security loopholes that hackers could exploit.
What is Port Scanning and Why Should You Care?
In the simplest terms, port scanning is like “knocking on doors” of a computer or network to see which ones are open and responsive. Each “door” represents a port, a communication endpoint used by applications and services.
But why is this important, you ask?
Think about it:
- For mechanics: Just like you wouldn’t want your garage door left open overnight, leaving ports open and unguarded invites trouble.
- From a technical standpoint: Open ports can be exploited by malicious actors to gain unauthorized access to your systems, steal sensitive data, or disrupt operations.
- Economically speaking: A security breach can be devastating, leading to financial losses, legal liabilities, and reputational damage.
 Port scanning analogy with car diagnostics
Port scanning analogy with car diagnostics
Diving Deeper: Understanding the Significance of Port Scanning Tools
Port scanning tools are indispensable for network administrators, security professionals, and even ethical hackers (the good guys!). These tools automate the process of probing a network, sending out packets of data to specific ports and analyzing the responses.
By using these tools, you can:
- Identify open ports: Discover which ports are open and listening for connections, indicating potentially vulnerable services.
- Fingerprint operating systems and services: Determine the type of operating system, applications, and versions running on a target system. This information helps tailor security measures and identify potential weaknesses.
- Test firewall rules: Verify that your firewall is configured correctly and blocking unauthorized access to specific ports.
- Conduct security audits: Regularly scan your network to identify and mitigate vulnerabilities before attackers can exploit them.
Common Port Scanning Techniques
Just like a skilled mechanic has various tools for diagnosing car problems, several port scanning techniques exist, each with its own approach:
- TCP Connect Scan: The most reliable but easily detectable method, establishing a full TCP connection to each port.
- SYN Scan (Stealth Scan): A more stealthy technique, only initiating a connection without completing it, making it harder to detect.
- UDP Scan: Used to scan UDP ports, often associated with services like DNS and DHCP.
- FIN Scan: Can bypass some firewalls but may not be reliable on all systems.
- Xmas Scan: Sends packets with multiple flags set, potentially revealing more information about the target system.
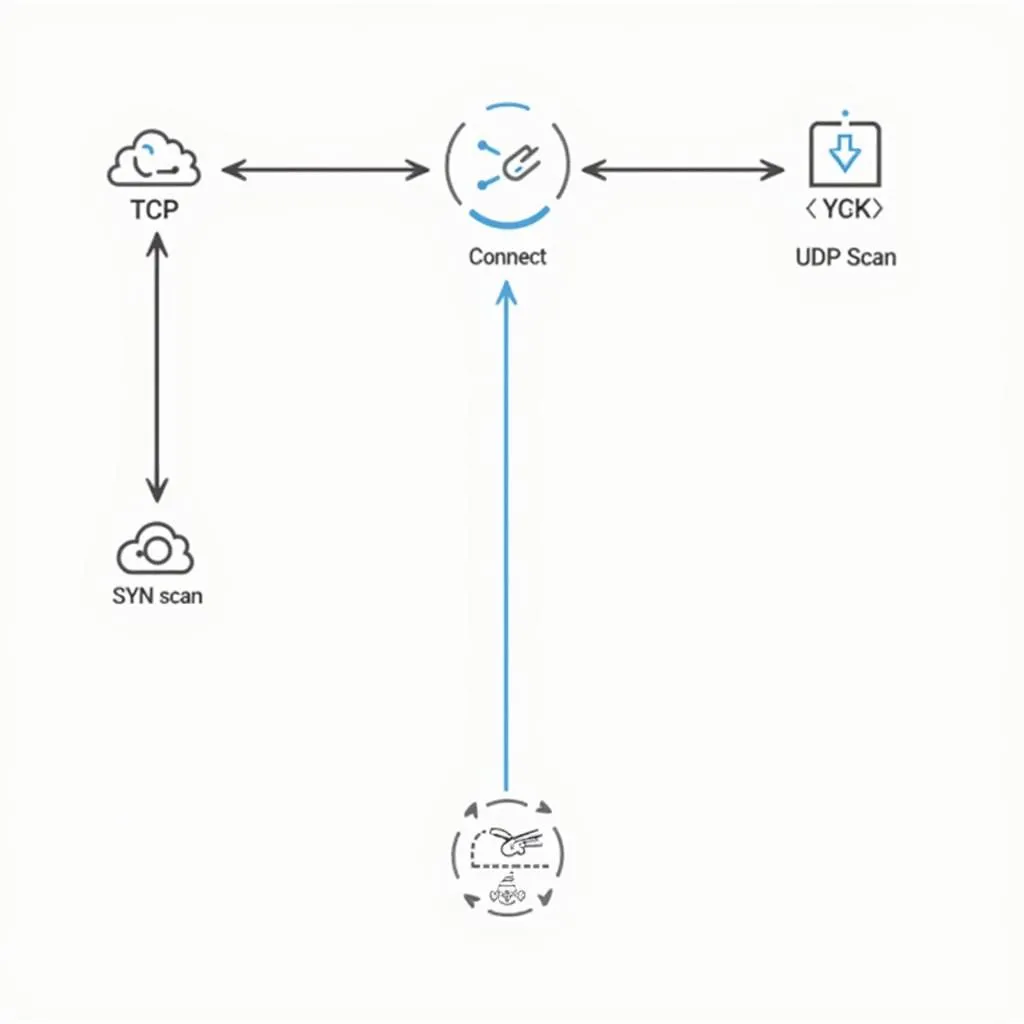 Visual representation of different port scanning techniques
Visual representation of different port scanning techniques
Top Port Scanning Tools in the Market
Choosing the right port scanning tool is crucial. Here are some popular options:
- Nmap (Network Mapper): A free, open-source, and highly versatile tool used by professionals worldwide. It offers a wide array of scanning techniques, making it suitable for both basic and advanced network exploration.
- Zenmap: A graphical user interface (GUI) for Nmap, providing a more user-friendly experience for those less comfortable with command-line tools.
- Angry IP Scanner: Another free and open-source network scanner, known for its speed and ease of use.
- Netcat (NC): A powerful and versatile networking tool that can be used for port scanning, banner grabbing, and even transferring files.
- Qualys Free Security Scan: A cloud-based vulnerability scanner that includes port scanning capabilities, ideal for small businesses and individuals.
Expert Insights and Real-World Applications
“Port scanning is not about being malicious; it’s about understanding your attack surface,” says John Miller, a cybersecurity expert and author of “The Network Security Handbook.” “Just like a mechanic uses a scanner to find and fix potential car problems before they become major issues, port scanning tools help organizations proactively identify and address network vulnerabilities.”
For instance, a car dealership in California recently used port scanning tools to uncover a security flaw in their Wi-Fi network. By identifying an open port associated with an outdated firmware version on their router, they were able to patch the vulnerability before any malicious activity occurred.
Beyond the Basics: Exploring Related Security Concepts
Port scanning is often just the first step in a comprehensive security assessment. Other important tools and techniques include:
- Vulnerability scanning: Identifies known weaknesses in software and systems, providing insights for remediation. (Learn more: Vulnerability Scanning Tools for Small Business: Cost & Comparison)
- Penetration testing: Simulates real-world attacks to exploit vulnerabilities and assess the effectiveness of security controls.
- Intrusion detection and prevention systems (IDPS): Monitor network traffic for suspicious activity and take action to block or mitigate threats.
 Diagram of interconnected network security tools and techniques
Diagram of interconnected network security tools and techniques
Expanding Your Knowledge: Further Questions and Resources
- What are the legal implications of port scanning?
- How can I interpret the results of a port scan?
- What are some best practices for securing open ports?
Explore our website for more in-depth articles on network security:
- Network Port Scanning Tools: https://diagxcar.com/network-port-scanning-tools/
- Tools Used to Detect Trojans by Scanning Ports: https://diagxcar.com/tools-used-to-detect-trojans-by-scanning-ports/
- IOC Scanning Tools: https://diagxcar.com/ioc-scanning-tools/
- Tools Used for Port Scanning: https://diagxcar.com/tools-used-for-port-scanning/
Need Help with Your Network Security?
Understanding and securing your network can be complex. If you’re feeling overwhelmed or need expert assistance with diagnostic tools and software, don’t hesitate to reach out. Contact us on Whatsapp at +84767531508. Our team of automotive and cybersecurity specialists is available 24/7 to help you diagnose and resolve any issues, keeping your systems running smoothly and securely.


