Security code scanning tools are essential for identifying vulnerabilities in your software before they can be exploited by malicious actors. In today’s interconnected world, where software vulnerabilities can have devastating consequences, utilizing these tools is no longer a luxury, but a necessity. They play a critical role in ensuring the safety and integrity of your applications and systems.
What are Security Code Scanning Tools?
Security code scanning tools are automated solutions that analyze source code, bytecode, or binaries to detect potential security flaws. These tools help developers identify and fix vulnerabilities early in the software development lifecycle, reducing the risk of costly breaches and reputational damage.
After the opening paragraph, we should delve deeper into the different types of security code scanning tools available. java source code security scanning tools are specifically designed to analyze Java codebases, while other tools offer broader language support.
Types of Security Code Scanning Tools
There are several types of security code scanning tools, each with its own strengths and weaknesses. Choosing the right tool depends on factors such as the programming languages used, the development environment, and the specific security requirements of the project. Some common categories include:
-
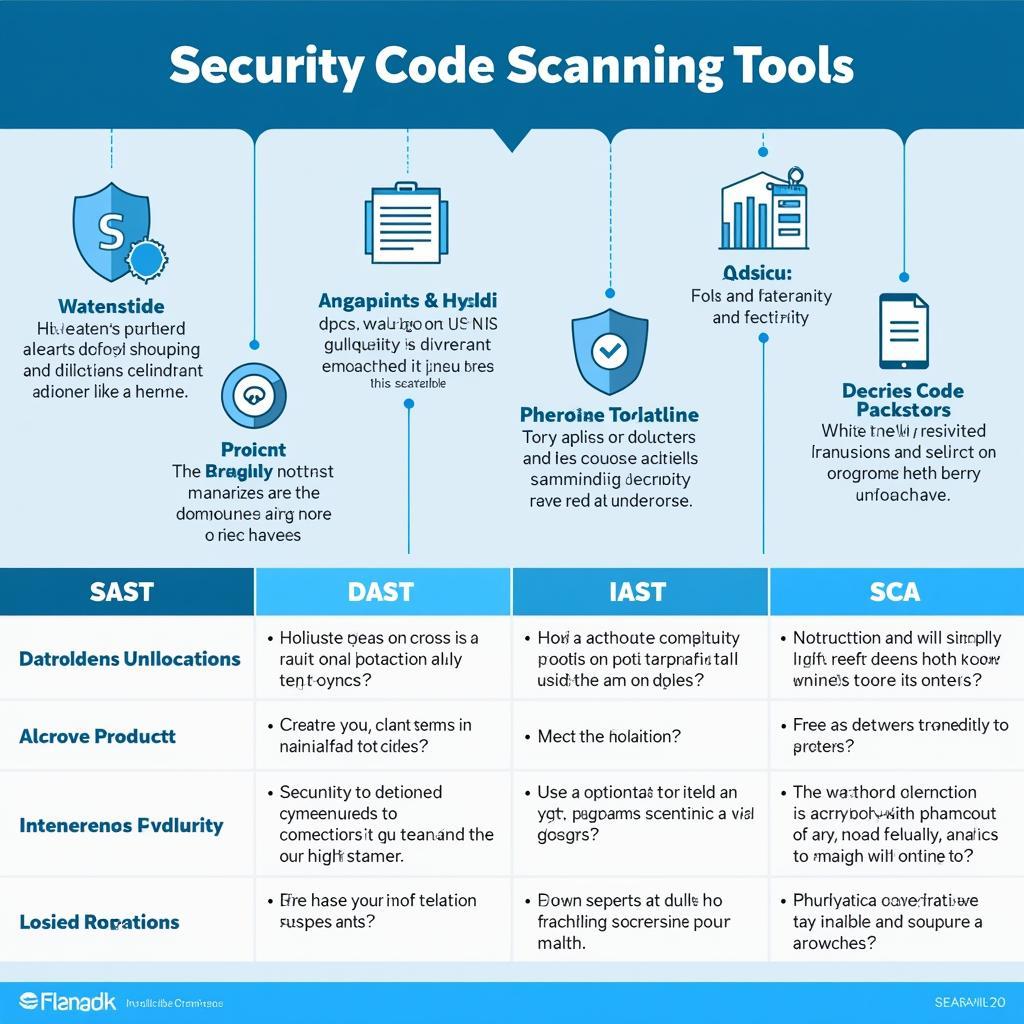
Static Application Security Testing (SAST): These tools analyze source code without actually executing it, looking for patterns and known vulnerabilities. They are particularly effective at identifying coding errors that could lead to security issues.
-
Dynamic Application Security Testing (DAST): DAST tools test running applications to identify vulnerabilities that are only apparent during runtime, such as injection flaws and authentication issues.
-
Interactive Application Security Testing (IAST): IAST tools combine aspects of both SAST and DAST, analyzing code while it is running to provide more comprehensive and accurate results.
-
Software Composition Analysis (SCA): SCA tools focus on identifying vulnerabilities in open-source and third-party components used in a software project.
 Types of Security Code Scanning Tools
Types of Security Code Scanning Tools
Why Use Security Code Scanning Tools?
Using code vulnerability scanning tools is crucial for a number of reasons, including:
-
Early Detection: Identifying vulnerabilities early in the development cycle significantly reduces the cost and effort required to fix them.
-
Improved Security Posture: Regular use of these tools helps organizations strengthen their overall security posture by proactively addressing potential weaknesses.
-
Compliance Requirements: Many industry regulations and standards require organizations to implement security scanning as part of their software development processes.
-
Reduced Risk of Breaches: By identifying and mitigating vulnerabilities, security scanning tools help minimize the risk of successful cyberattacks.
 Benefits of Using Security Code Scanning Tools
Benefits of Using Security Code Scanning Tools
“Proactive vulnerability management is no longer optional. Security code scanning tools are a fundamental component of a robust security strategy,” says John Smith, Senior Security Architect at CyberSafe Solutions.
How to Choose the Right Security Code Scanning Tools
Choosing the right static security scanning tools depends on several factors. Consider the following when making your decision:
-
Programming Languages: Ensure the tool supports the languages used in your projects. Some tools specialize in specific languages, such as Java, while others offer broader support. Check out resources for specific languages, like java code scanning tools.
-
Integration with Development Environment: Seamless integration with your existing development tools and workflows is crucial for efficient and effective use.
-
Reporting and Analysis Capabilities: Choose a tool that provides clear and concise reports, allowing developers to quickly understand and address identified vulnerabilities.
-
Cost and Scalability: Consider the cost of the tool and its ability to scale to meet the needs of your organization as it grows.
“Selecting the right security code scanning tool is a critical decision. It’s essential to carefully evaluate your specific needs and choose a tool that aligns with your development environment and security requirements,” advises Jane Doe, Cybersecurity Consultant at SecureTech Inc.
Conclusion
Security code scanning tools are indispensable for developing secure and reliable software. By integrating these tools into your development process, you can proactively identify and mitigate vulnerabilities, reducing the risk of costly breaches and enhancing the overall security posture of your organization. Don’t wait until it’s too late – implement security code scanning today.
FAQ
- What is the difference between SAST and DAST?
- How often should I run security scans?
- What are the benefits of using SCA tools?
- How can I integrate security scanning into my CI/CD pipeline?
- What are some common vulnerabilities found by security scanning tools?
- Are open-source security scanning tools effective?
- How can I choose the right security scanning tool for my organization?
Need help with security code scanning or want to learn more about microsoft code scanning tools? Contact us on WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. Our 24/7 customer support team is ready to assist you.


