Network vulnerability scanning tools are essential for maintaining a robust security posture in today’s interconnected world. They help identify weaknesses in your network before malicious actors can exploit them, preventing data breaches and costly downtime. This guide will delve into the importance of these tools, exploring their functionalities, benefits, and how to choose the right one for your specific needs. Learn more about how network vulnerability scanning tools can safeguard your valuable data and ensure the integrity of your network infrastructure.
Understanding Network Vulnerability Scanning Tools
Network vulnerability scanners automate the process of proactively identifying security weaknesses in your network devices, software, and configurations. They do this by simulating attacks and analyzing the network’s response. These tools scan for known vulnerabilities, including outdated software, open ports, misconfigurations, and weak passwords. Identifying these weaknesses allows you to implement appropriate security measures before they can be exploited by cybercriminals. For IT professionals and businesses, these tools are no longer a luxury but a necessity for survival in the digital landscape. Check out our resources on the best network vulnerability scanning tools to learn more.
How Network Vulnerability Scanners Work
These tools typically work by sending probes to target systems and analyzing the responses. They compare the results with a database of known vulnerabilities and flag any potential weaknesses. This process includes checking for open ports, identifying running services, and testing for common exploits.
Types of Network Vulnerability Scans
Different types of scans cater to specific security needs. These include:
- Uncredentialed scans: These scans simulate an external attacker with no prior knowledge of the network.
- Credentialed scans: These scans use valid user credentials to simulate an internal attacker or authorized user, providing a more in-depth analysis.
- Passive scans: These scans monitor network traffic without actively sending probes, minimizing disruption to network operations.
- Active scans: These scans actively probe the network, providing a more comprehensive assessment of vulnerabilities.
Why Use a Network Vulnerability Scanning Tool?
Using a network vulnerability scanning tool provides numerous benefits, including:
- Proactive Security: Identify vulnerabilities before attackers do.
- Reduced Risk: Minimize the risk of data breaches and system compromises.
- Compliance: Meet regulatory requirements and industry best practices.
- Cost Savings: Prevent costly data breaches and downtime.
- Improved Security Posture: Strengthen your overall network security.
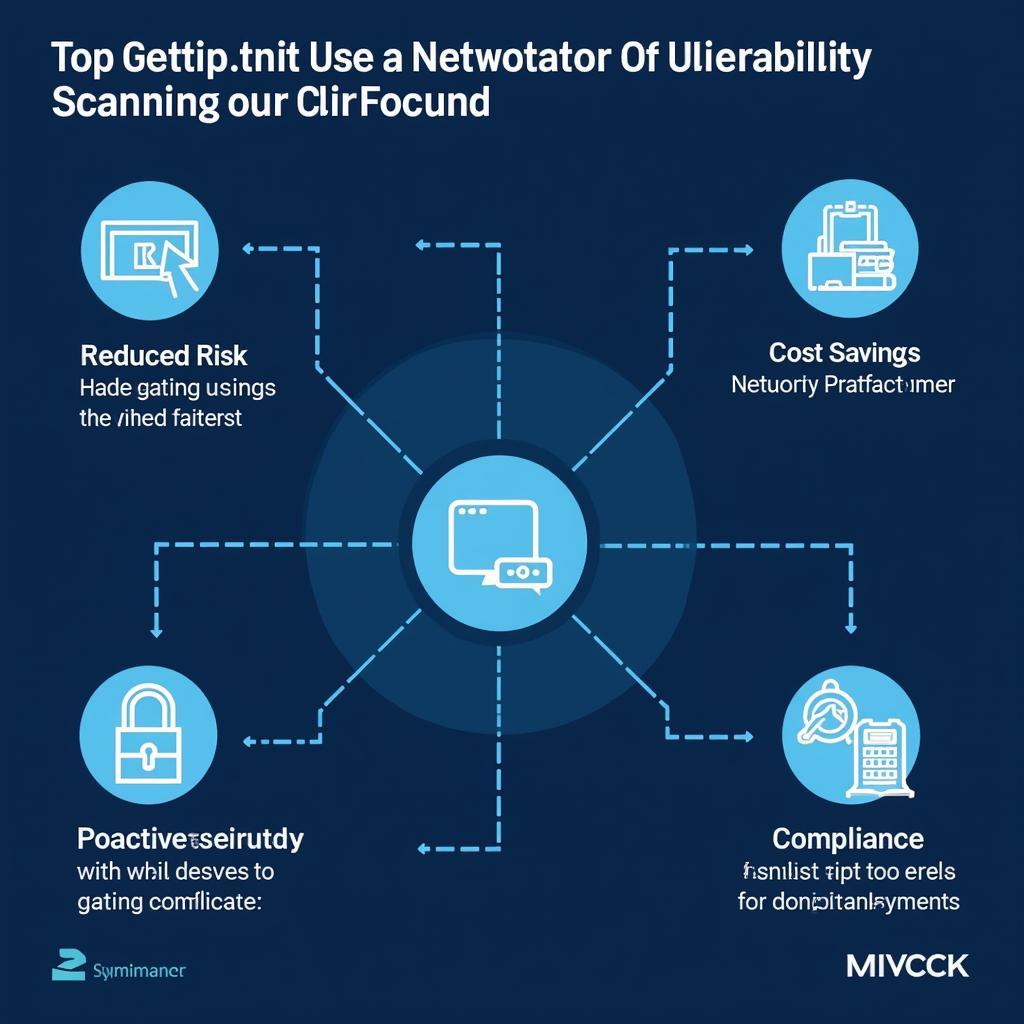 Benefits of Network Vulnerability Scanning
Benefits of Network Vulnerability Scanning
Choosing the Right Network Vulnerability Scanning Tool
Selecting the appropriate tool requires careful consideration of several factors, including:
- Ease of use: The tool should be intuitive and easy to navigate.
- Scanning capabilities: Ensure the tool covers the required scan types and vulnerabilities.
- Reporting and analysis: The tool should provide comprehensive and actionable reports.
- Cost: Consider the overall cost, including licensing fees and maintenance.
- Scalability: Choose a tool that can grow with your network.
You can explore various network vulnerability scanning tools for IT and free network vulnerability scanning tools available on the market. For enterprise networks, specific vulnerability scanning tools for enterprise network can be considered. Nessus is a popular scanning tool Nessus known for its comprehensive vulnerability database.
Conclusion
Network vulnerability scanning tools are crucial for maintaining a strong security posture in today’s threat landscape. By proactively identifying and addressing vulnerabilities, these tools can significantly reduce the risk of cyberattacks and protect your valuable data. Choosing the right tool and implementing a regular scanning schedule are essential steps towards building a robust and secure network infrastructure. Implement a network vulnerability scanning tool today and safeguard your digital assets.
FAQ
- What is a network vulnerability scan?
- Why is network vulnerability scanning important?
- How often should I scan my network for vulnerabilities?
- What are the different types of network vulnerability scans?
- How do I choose the right network vulnerability scanning tool?
- What are the benefits of using a network vulnerability scanning tool?
- Are there free network vulnerability scanning tools available?
Common Scenarios and Questions:
-
Scenario: A company experiences a data breach due to an unpatched vulnerability.
-
Question: How could a network vulnerability scanning tool have prevented this?
-
Scenario: A small business owner is concerned about the cost of network security.
-
Question: Are there affordable network vulnerability scanning solutions available for small businesses?
-
Scenario: An IT manager needs to comply with industry regulations.
-
Question: How can a network vulnerability scanning tool help with compliance?
Further Exploration:
For more information on network vulnerability scanning tools, explore the following resources on our website:
- Network vulnerability scanning tools for IT
- Free network vulnerability scanning tools
- Best network vulnerability scanning tools
Contact Us
For assistance with your network security needs, please contact us via WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. Our customer support team is available 24/7.


