Network server scanning tools are essential for maintaining the security and performance of any network infrastructure. They provide a crucial first line of defense against cyber threats and help identify vulnerabilities before they can be exploited. By understanding the capabilities and benefits of these tools, businesses and individuals can protect their valuable data and ensure the stability of their network operations. In this guide, we will explore the world of network server scanning tools and discuss how to choose the right one for your specific needs.
Understanding the Importance of Network Server Scanning Tools
Network server scanning tools go beyond simple network mapping. They delve deeper into the intricacies of your network, identifying open ports, active services, and potential vulnerabilities that could be exploited by malicious actors. These tools offer valuable insights into your network topology, helping you understand the relationships between different devices and servers, and pinpoint potential weaknesses. Regular scanning is crucial for proactive security management, allowing you to address vulnerabilities before they become a problem.
This proactive approach is especially vital in today’s rapidly evolving cyber threat landscape. With new vulnerabilities discovered daily, regular scanning helps ensure your network stays ahead of potential threats. Furthermore, these tools can aid in compliance with industry regulations, such as PCI DSS, by providing documented evidence of your security posture.
hard disk scan tools are also important for overall system health.
Types of Network Server Scanning Tools
There are various types of network server scanning tools, each with its own strengths and weaknesses:
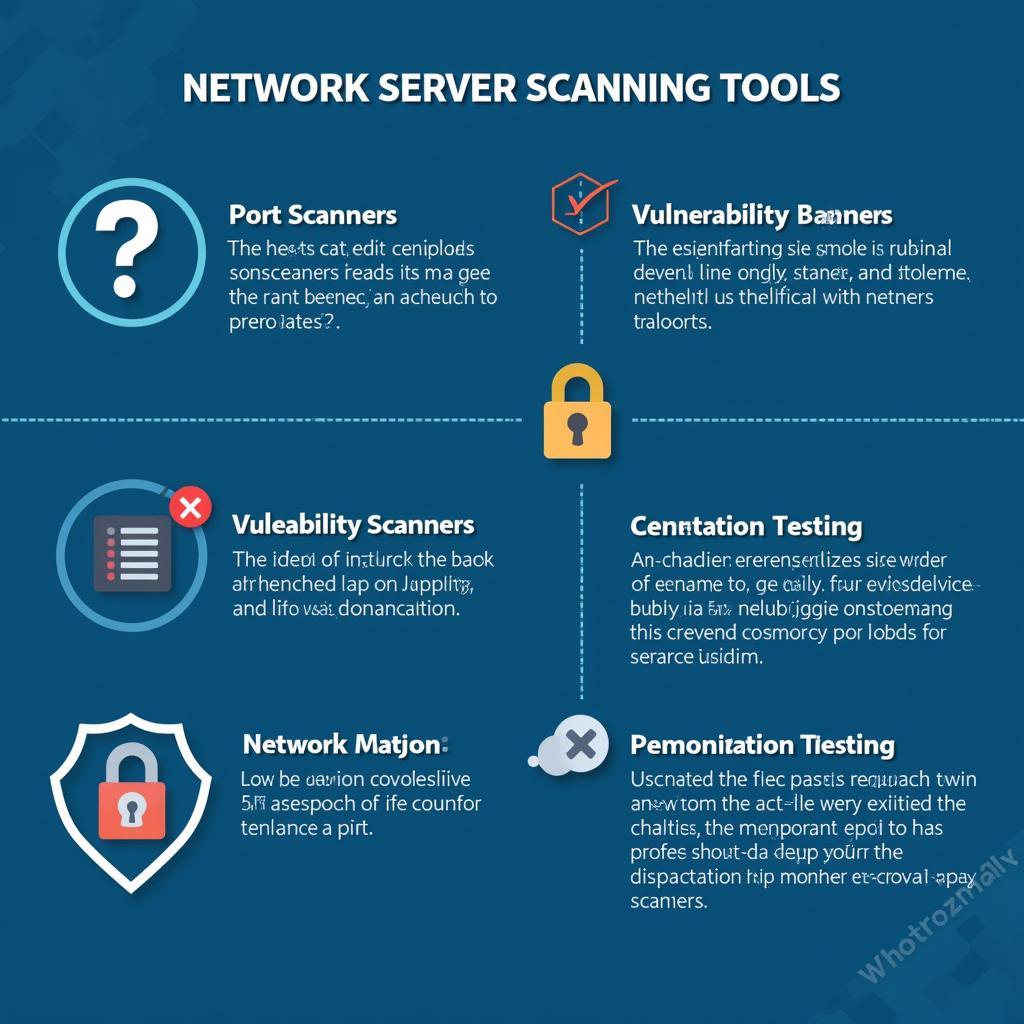
- Port Scanners: These tools identify open ports on a server, indicating which services are running and potentially vulnerable.
- Vulnerability Scanners: These tools go beyond port scanning to identify specific vulnerabilities in software and configurations. They often include databases of known vulnerabilities and can provide detailed reports on potential risks.
- Network Mappers: These tools create a visual representation of your network, showing the connections between devices and servers. This can be useful for identifying rogue devices or unauthorized connections.
- Penetration Testing Tools: These tools simulate real-world attacks to identify vulnerabilities and test the effectiveness of your security measures.
tools vulnerability scanning can provide a comprehensive overview of your system’s security weaknesses.
 Types of Network Server Scanning Tools
Types of Network Server Scanning Tools
Key Features to Look for in a Network Server Scanning Tool
When selecting a network server scanning tool, consider the following key features:
- Comprehensive Scanning Capabilities: The tool should be able to perform a wide range of scans, including port scanning, vulnerability scanning, and network mapping.
- Automated Scanning: The tool should allow for automated, scheduled scans to ensure regular checks without manual intervention.
- Detailed Reporting: The tool should provide clear and concise reports that outline identified vulnerabilities and offer remediation advice.
- Ease of Use: The tool should be user-friendly, even for those without extensive technical expertise.
- Integration with Other Security Tools: The tool should integrate seamlessly with other security tools, such as firewalls and intrusion detection systems.
How to Use Network Server Scanning Tools Effectively
To maximize the effectiveness of your network server scanning tools, follow these best practices:
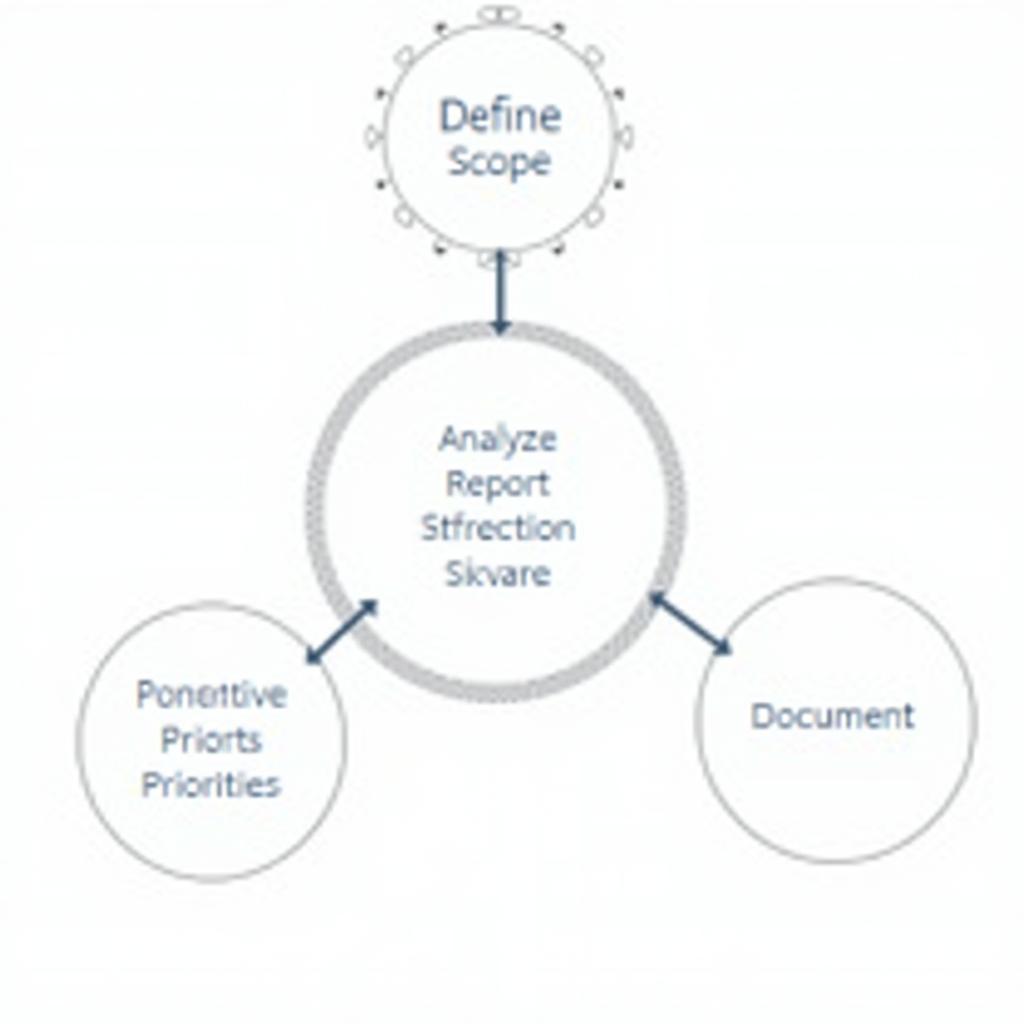
- Define Your Scope: Clearly define the scope of your scans, including which servers and networks you want to assess.
- Schedule Regular Scans: Automate scans to occur regularly, ideally weekly or monthly, to stay ahead of emerging threats.
- Analyze Reports Carefully: Review scan reports thoroughly to understand identified vulnerabilities and their potential impact.
- Prioritize Remediation: Prioritize addressing critical vulnerabilities based on their severity and potential impact.
- Document Your Findings: Maintain detailed records of your scans and remediation efforts for compliance and auditing purposes.
 Effective Network Server Scanning Process
Effective Network Server Scanning Process
vulnerability pci scanning tool can help businesses maintain PCI compliance.
What are the benefits of using Network Server Scanning Tools?
Using network server scanning tools offers a multitude of benefits:
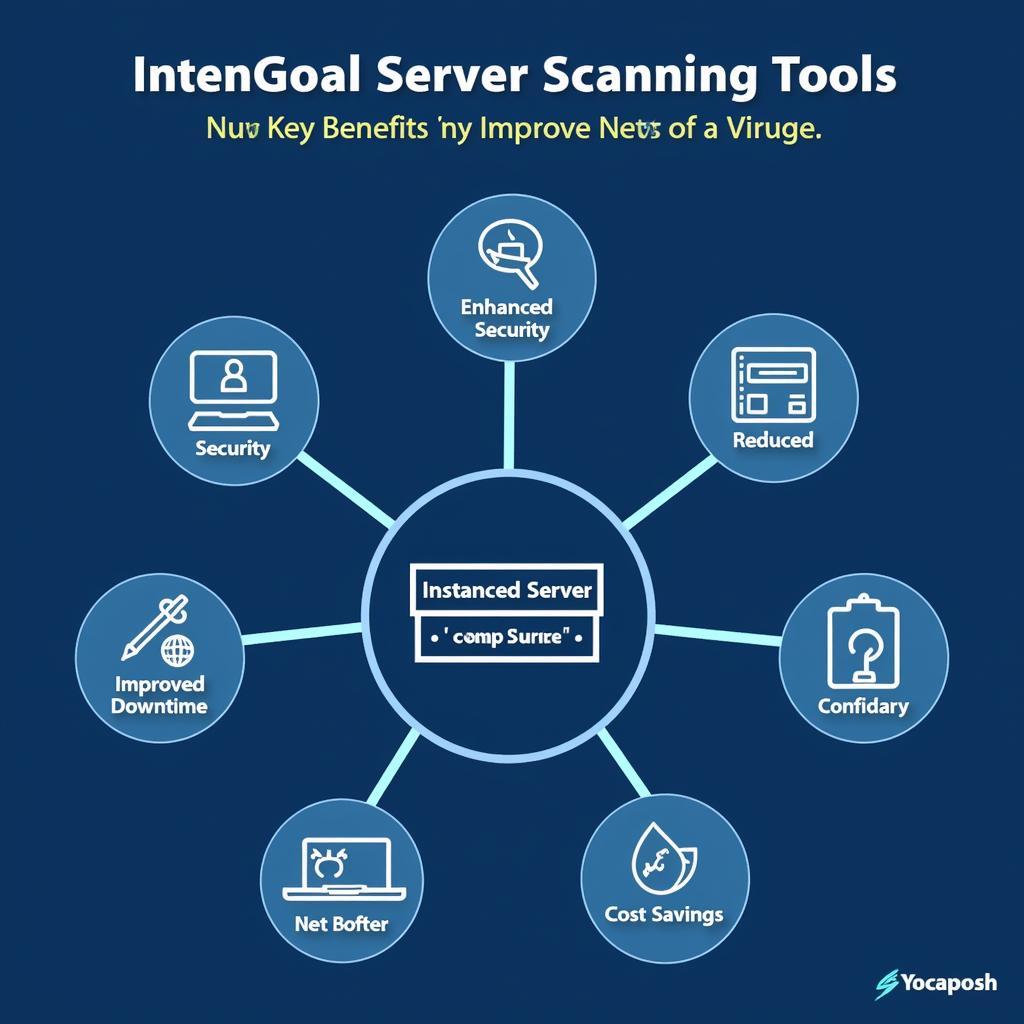
- Enhanced Security: Proactive identification and remediation of vulnerabilities significantly strengthens your network’s security posture.
- Improved Compliance: Regular scanning helps demonstrate compliance with industry regulations and security standards.
- Reduced Downtime: By identifying and addressing potential problems before they cause outages, you can minimize network downtime.
- Cost Savings: Preventing security breaches and downtime can save your organization significant costs in the long run.
- Better Network Performance: Identifying and resolving network bottlenecks can improve overall network performance.
“Regularly using network server scanning tools is like having a dedicated security guard for your network,” says John Smith, Senior Network Security Consultant at CyberSecure Solutions. “It helps you identify and address vulnerabilities before they can be exploited, ensuring the safety and stability of your network.”
rapid fire tools internal vulnerability scan offers a powerful solution for internal network vulnerability assessment.
 Benefits of Network Server Scanning Tools
Benefits of Network Server Scanning Tools
tools for scanning website vulnerabilities are also crucial for maintaining online security.
Conclusion
Network server scanning tools are indispensable for maintaining a secure and efficient network infrastructure. By understanding the different types of tools available, their key features, and best practices for their use, you can effectively protect your network from evolving cyber threats. Implementing a robust scanning strategy is crucial for proactive security management and ensuring the long-term stability of your network operations. Investing in the right network server scanning tools is a vital step towards building a resilient and secure network environment.
FAQ
- How often should I scan my network servers?
- What are the different types of network server scanning tools available?
- How do I choose the right network server scanning tool for my needs?
- What should I do after identifying vulnerabilities in my network?
- How can network server scanning tools help me comply with industry regulations?
- What are the cost benefits of using network server scanning tools?
- Can I use network server scanning tools on my home network?
Common Scenarios & Questions:
- Scenario: A company experiences a data breach due to an unpatched vulnerability. Question: How could network server scanning tools have prevented this?
- Scenario: A network administrator needs to identify all devices connected to the network. Question: Which type of network server scanning tool is most suitable for this task?
- Scenario: A small business owner is concerned about the cost of network security. Question: Are there affordable network server scanning tools available for small businesses?
Further Reading & Related Resources:
- Check out our other blog posts on network security best practices.
- Learn more about vulnerability management and risk assessment.
- Explore our resources on choosing the right security tools for your business.
Need help? Contact us via WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. Our customer support team is available 24/7.


