Heartbleed, a serious vulnerability discovered in 2014, sent shockwaves through the internet. This flaw in the OpenSSL cryptographic software library allowed attackers to steal sensitive information, including usernames, passwords, and even encryption keys, directly from the memory of affected systems. A heartbleed scan tool is essential for identifying and mitigating this vulnerability. Understanding how these tools work and deploying them effectively is crucial for maintaining the security of your online presence.
Businesses and individuals alike need to understand the implications of Heartbleed and take proactive steps to protect their systems. This article will delve into the specifics of the Heartbleed vulnerability, explain how heartbleed scan tools work, discuss various types of scanners available, and guide you on how to choose the right one for your needs. We will also cover best practices for using these tools and offer tips for maintaining a secure online environment.
Understanding the Heartbleed Vulnerability
Heartbleed exploits a flaw in the heartbeat extension of the OpenSSL protocol. This extension allows systems to periodically check if the connection is still alive by sending a small amount of data, called a “heartbeat,” and expecting a response. The vulnerability lies in how OpenSSL handled the heartbeat requests. An attacker could send a malicious heartbeat request, asking for a larger chunk of data than they were supposed to receive. OpenSSL, without proper validation, would then send back the requested amount of data, potentially including sensitive information from the server’s memory.
This vulnerability allows attackers to bypass encryption and steal private data without leaving a trace. The implications of this are severe, potentially compromising user accounts, financial transactions, and even confidential communications. Hence, using a reliable heartbleed scan tool is paramount. After the initial discovery, many systems were patched, but some remain vulnerable.
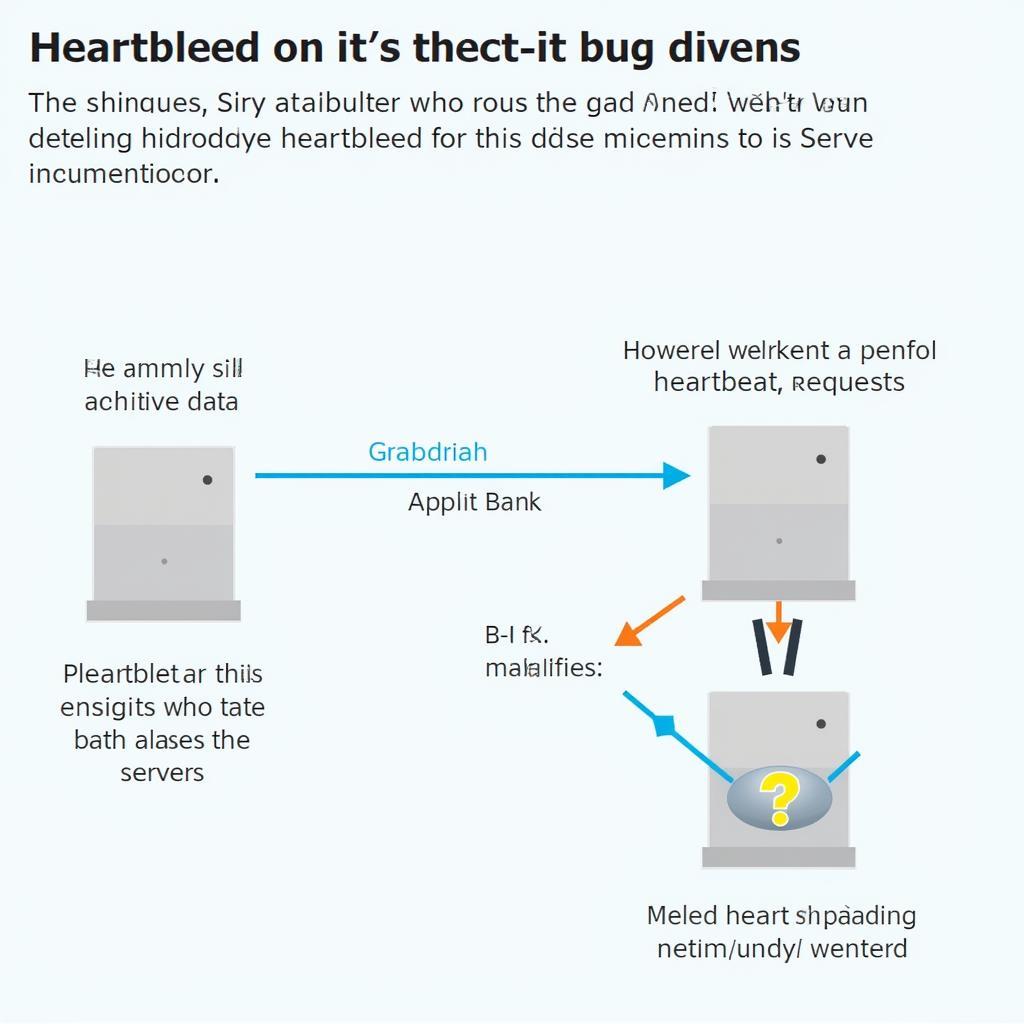 Heartbleed Vulnerability Explained
Heartbleed Vulnerability Explained
How Does a Heartbleed Scan Tool Work?
A heartbleed scan tool simulates the malicious heartbeat request that exploits the vulnerability. It sends this request to a target system and analyzes the response. If the server is vulnerable, it will respond with more data than requested, confirming the presence of the Heartbleed bug. These tools typically check various ports and services that might be using the vulnerable version of OpenSSL. Some openssl scan tool offer advanced features, such as vulnerability scoring and reporting, to help prioritize remediation efforts.
Choosing the Right Heartbleed Scan Tool
Selecting the appropriate heartbleed scan tool depends on several factors, including the size and complexity of your network, your technical expertise, and your budget. There are free online scanners available for quick checks, as well as more comprehensive commercial tools that offer in-depth analysis and reporting. When choosing a tool, consider the following:
- Accuracy: The tool should accurately identify vulnerable systems without producing false positives or negatives.
- Ease of use: The interface should be intuitive and easy to navigate, even for non-technical users.
- Features: Consider features such as automated scanning, reporting, and integration with other security tools.
- Support: Ensure the vendor provides adequate support and documentation.
Best Practices for Using Heartbleed Scan Tools
While using a heartbleed scan tool is crucial, it’s equally important to follow best practices to ensure effective scanning and remediation.
- Regular Scanning: Schedule regular scans to identify any new vulnerabilities that may arise.
- Patching: Immediately patch any vulnerable systems identified by the scan. This is the most effective way to mitigate the risk.
- Password Changes: Advise users to change their passwords on affected systems, even if no evidence of compromise exists.
- Monitor Network Traffic: Implement network monitoring tools to detect any suspicious activity that might indicate an attack.
- Consider an ssl scanning tool for comprehensive security checks.
Protecting Your Systems Beyond Heartbleed
While Heartbleed was a significant vulnerability, it highlights the importance of ongoing security vigilance. Staying informed about new threats and implementing best practices is crucial for maintaining a secure online environment. Consider exploring resources like linux network scan tool tls for enhanced network security.
“Regular vulnerability scanning is not just a best practice; it’s a necessity in today’s interconnected world,” says Alex Thompson, Senior Cybersecurity Analyst at SecureTech Solutions. “Heartbleed taught us a valuable lesson about the importance of proactive security measures.”
Conclusion
Heartbleed remains a stark reminder of the potential impact of software vulnerabilities. Using a heartbleed scan tool is a vital step in protecting your systems from this specific threat. By understanding the vulnerability, choosing the right tool, and following best practices, you can significantly reduce your risk and maintain a secure online environment. Remember that regular scanning and patching are crucial for staying ahead of evolving threats.
FAQ
- What is Heartbleed?
- How does Heartbleed work?
- How can I detect Heartbleed?
- How can I fix Heartbleed?
- Is Heartbleed still a threat?
- What are the consequences of Heartbleed?
- How can I prevent future vulnerabilities like Heartbleed?
“Proactive security measures are essential in today’s rapidly evolving threat landscape,” adds Maria Sanchez, Security Consultant at CyberSafe Solutions. “Utilizing the right tools and staying informed is key to mitigating risks effectively.”
Have you explored other vulnerability scanning tools? Read more about network security best practices on our website.
Contact us for support: WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. We offer 24/7 customer support.


