CVE scanning tools are essential for identifying and mitigating security risks in software and systems. These tools automate the process of checking for known vulnerabilities, helping organizations proactively address potential threats before they can be exploited. This proactive approach is crucial in today’s interconnected world, where cyberattacks are becoming increasingly sophisticated. Using a CVE scanner can significantly enhance your security posture.
Understanding CVE Scanning Tools
What exactly are CVE scanning tools, and why are they so important? CVE stands for Common Vulnerabilities and Exposures, a system for publicly identifying and cataloging security flaws. CVE scanning tools leverage this database to detect known vulnerabilities in your applications, operating systems, and hardware. By automating this process, these tools save valuable time and resources while ensuring comprehensive coverage. They provide a crucial layer of defense against cyber threats, enabling organizations to identify and address weaknesses before attackers can exploit them. Choosing the right cve scanning tools can be a game-changer for your security strategy.
How Do CVE Scanners Work?
CVE scanners typically work by comparing the software and systems they scan against the CVE database. They identify known vulnerabilities and report them, often with details about the severity and potential impact of each flaw. This allows security teams to prioritize remediation efforts and effectively allocate resources. The process usually involves analyzing software versions, configurations, and dependencies to identify potential weaknesses.
“CVE scanning is not a one-time activity but an ongoing process. Regular scans are crucial to stay ahead of emerging threats and maintain a strong security posture,” says cybersecurity expert, Dr. Amelia Chen, CISSP.
 CVE Scanner Analyzing Software Vulnerabilities
CVE Scanner Analyzing Software Vulnerabilities
Choosing the Right CVE Scanning Tool
Selecting the appropriate CVE scanning tool can be challenging. Factors to consider include the specific needs of your organization, the types of systems you need to scan, and the level of automation you require. Some tools specialize in specific operating systems or applications, while others offer broader coverage. Finding the right tool for your environment is essential for effective vulnerability management. Consider exploring options like nessus scanning tool download for robust vulnerability scanning capabilities.
Key Features to Look For
When evaluating CVE scanning tools, look for essential features such as comprehensive coverage of the CVE database, regular updates, accurate vulnerability detection, and clear reporting. Prioritize tools that integrate seamlessly with your existing security infrastructure and offer customization options to tailor the scanning process to your specific requirements. For containerized environments, tools like docker vulnerability scanning tools and docker security scanning tools are invaluable.
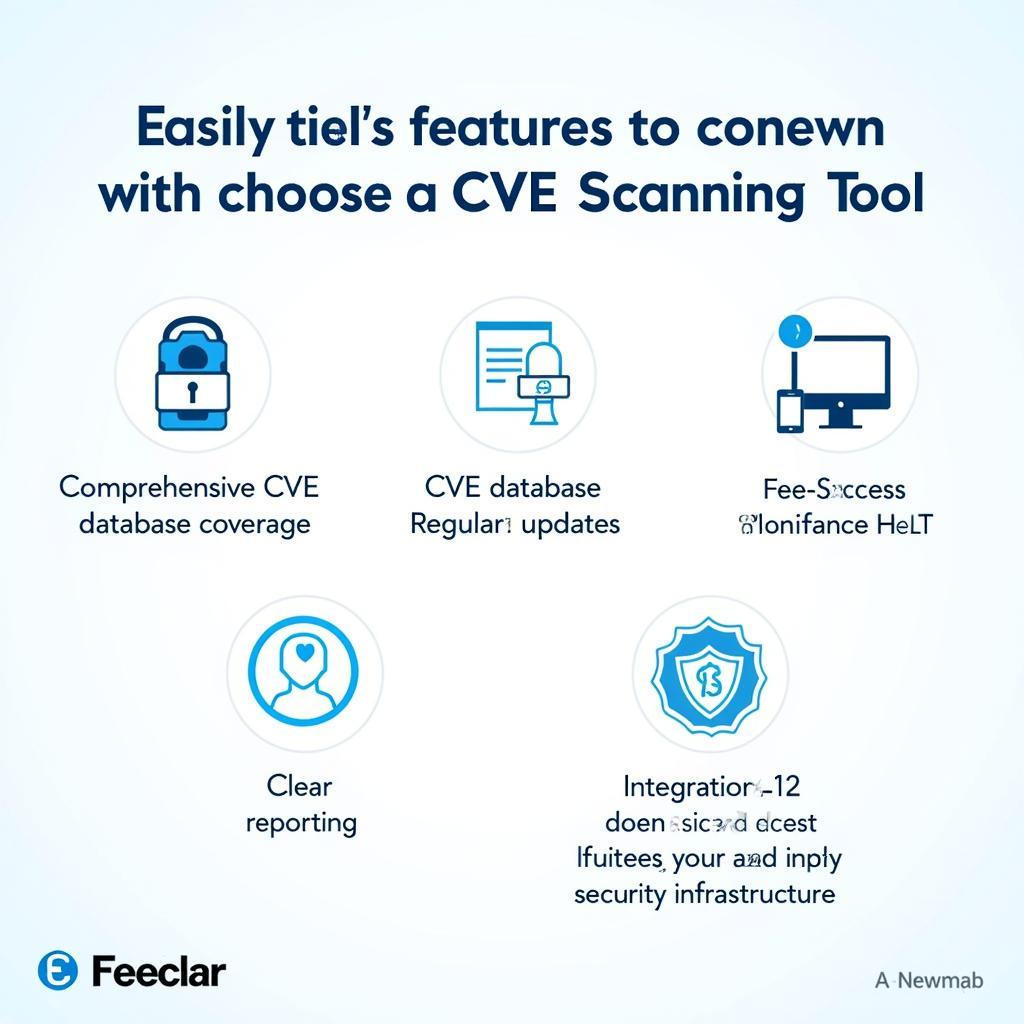 Key Features of CVE Scanning Tools
Key Features of CVE Scanning Tools
Best Practices for CVE Scanning
Effective CVE scanning requires more than just choosing the right tool. It’s also crucial to implement best practices, such as regular scanning, prioritizing vulnerabilities based on severity, and establishing a clear remediation process. Integrating CVE scanning into your development pipeline and automating security updates can significantly improve your overall security posture. Explore resources like best container scanning tools for best practices in container security.
Integrating CVE Scanning into Your Workflow
Integrating CVE scanning into your existing workflows can streamline the vulnerability management process. This can involve automating scans as part of your CI/CD pipeline, incorporating vulnerability assessment into your change management process, and establishing regular reporting procedures to track progress and identify trends. By making CVE scanning a routine part of your operations, you can ensure continuous security improvement.
“Integrating CVE scanning into your development lifecycle is crucial for shifting security left and proactively addressing vulnerabilities early in the development process,” advises David Lee, a leading software security consultant.
 Integrating CVE Scanning into Workflow
Integrating CVE Scanning into Workflow
Conclusion
CVE scanning tools are indispensable for any organization seeking to strengthen its security posture. By automating the process of identifying and mitigating known vulnerabilities, these tools provide a crucial layer of defense against increasingly sophisticated cyber threats. Selecting the right tool, implementing best practices, and integrating CVE scanning into your existing workflows are key steps in building a robust and resilient security program. By proactively addressing vulnerabilities, you can protect your systems, data, and reputation. Choosing the right CVE scanning tool is the first step.
FAQ
- What is a CVE? A CVE (Common Vulnerabilities and Exposures) is a standardized system for identifying and cataloging publicly known security vulnerabilities.
- Why is CVE scanning important? CVE scanning is essential for proactively identifying and mitigating security risks in software and systems.
- How often should I perform CVE scans? Regular CVE scans are crucial, ideally performed on a continuous or scheduled basis depending on the risk level of your systems.
- What are some popular CVE scanning tools? Popular CVE scanning tools include Nessus, OpenVAS, and QualysGuard.
- What are some best practices for CVE scanning? Best practices include regular scanning, prioritizing vulnerabilities, and establishing a clear remediation process.
- How can I integrate CVE scanning into my workflow? Integrate CVE scanning into your CI/CD pipeline and change management processes.
- Where can I find more information about CVE scanning? Resources like the National Vulnerability Database (NVD) and various security blogs provide valuable information on CVE scanning.
Need assistance with choosing the right CVE scanning solution or implementing effective vulnerability management strategies? Contact us via WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. Our 24/7 customer support team is ready to help.
You might also be interested in other articles on our website about topics like network security and penetration testing.


