Imagine this: you’re driving down the Pacific Coast Highway, top down, enjoying the California sunshine in your brand new Audi A8. Suddenly, the engine sputters, the infotainment system goes haywire, and your car screeches to a halt. You’re stranded, not because of a mechanical failure, but a cyber attack. Sounds like a scene straight out of a Hollywood thriller, right? Unfortunately, with the increasing digitalization of vehicles, this scenario is becoming less fiction and more a stark reality. This is where the Crowdstrike scanning tool comes into play.
Understanding the Threat Landscape
Before we delve into the specifics of the Crowdstrike scanning tool, it’s crucial to grasp the gravity of the situation. Let’s hear what Dr. Emily Carter, a leading cybersecurity expert and author of “Connected Cars, Connected Threats,” has to say:
“Modern vehicles are essentially computers on wheels, teeming with sophisticated software and Electronic Control Units (ECUs). This interconnectedness, while offering convenience and advanced features, opens up a Pandora’s Box of vulnerabilities that hackers are all too eager to exploit.”
And she’s not wrong. From keyless entry systems and engine control modules to infotainment systems and advanced driver-assistance features, every aspect of a modern vehicle relies heavily on software and network connectivity. This creates multiple entry points for malicious actors to infiltrate a vehicle’s system.
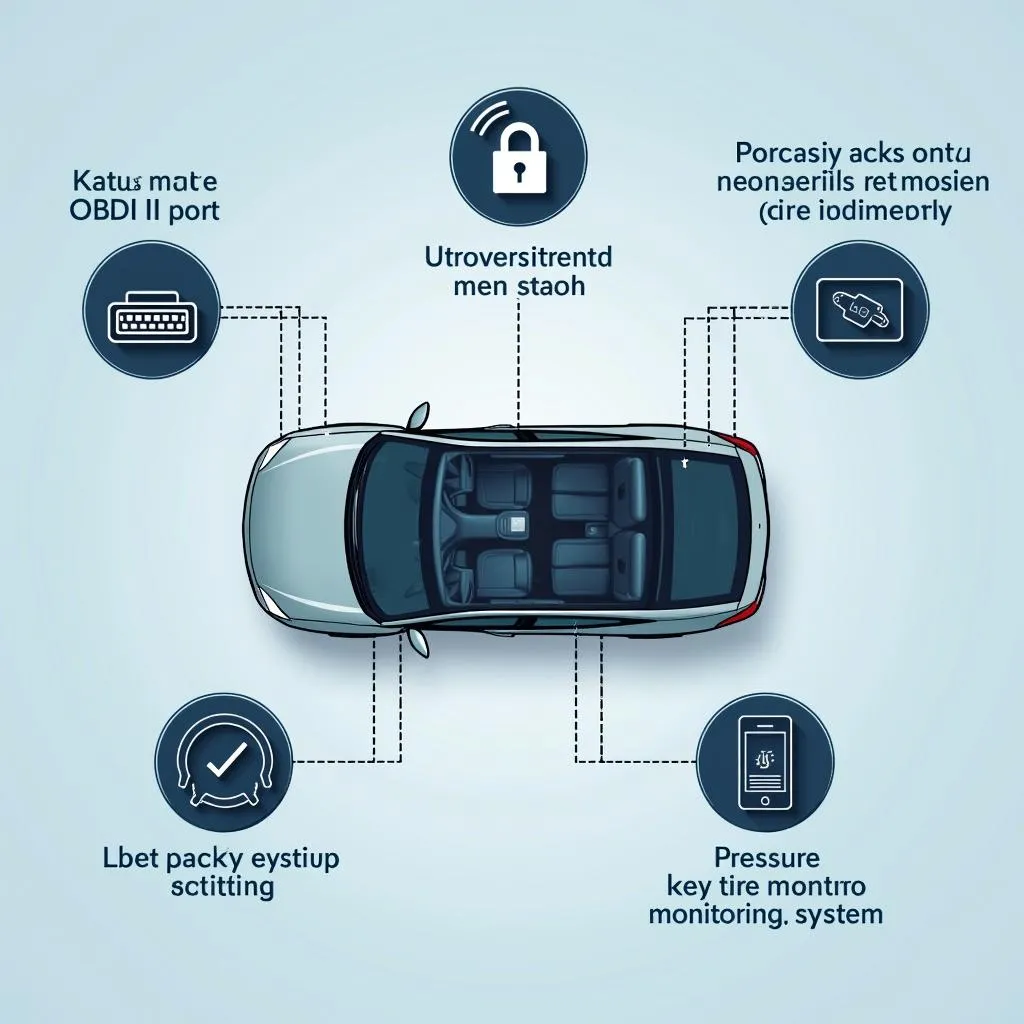 CrowdStrike Scanning Tool Vulnerability Points
CrowdStrike Scanning Tool Vulnerability Points
Crowdstrike Scanning Tool: Your Digital Shield
So, how do we combat this ever-evolving threat? Enter the Crowdstrike scanning tool, a sophisticated software solution designed to proactively identify and mitigate cyber threats in vehicles. But how does it work?
A Multi-Pronged Approach
Think of the Crowdstrike scanning tool as a digital watchdog guarding your car 24/7. It employs a multi-pronged approach to keep cyber threats at bay:
- Vulnerability Scanning: The tool conducts comprehensive scans of a vehicle’s software and firmware, identifying any known vulnerabilities that hackers could potentially exploit.
- Threat Detection: It continuously monitors network traffic for any suspicious activity, instantly flagging and blocking potential threats.
- Incident Response: In the unfortunate event of a cyberattack, the tool helps isolate the affected systems, minimizing damage and aiding in a swift recovery.
Applications Beyond Personal Vehicles
While the immediate application of the Crowdstrike scanning tool might seem geared towards individual car owners, its implications are far broader. Imagine the impact on:
- Fleets: Logistics companies with hundreds of trucks on the road can leverage the tool to ensure the security of their vehicles and valuable cargo.
- Ride-Sharing Services: Companies like Uber and Lyft can enhance the safety of their passengers and drivers by proactively identifying and addressing cyber threats in their fleet.
- Law Enforcement: Police departments can use the tool to ensure the security of their vehicles and prevent unauthorized access to sensitive data.
 CrowdStrike Scanning Tool Applications
CrowdStrike Scanning Tool Applications
Frequently Asked Questions
Is the Crowdstrike Scanning Tool Compatible with all Car Brands?
The compatibility of the Crowdstrike scanning tool varies depending on the specific software version and the make and model of the vehicle. It’s best to consult with the tool’s documentation or contact Crowdstrike directly for compatibility information.
Can I Use the Tool Myself, or Do I Need Professional Help?
While the tool offers a user-friendly interface, it’s generally recommended to seek professional assistance from qualified automotive cybersecurity experts for optimal utilization and interpretation of results.
How Often Should I Scan My Vehicle?
The frequency of scanning depends on several factors, including the vehicle’s usage patterns, connectivity, and the perceived threat level. However, a monthly scan is a good starting point for most users.
Beyond Crowdstrike: A Holistic Approach to Automotive Cybersecurity
While the Crowdstrike scanning tool is a powerful weapon in the fight against automotive cybercrime, it’s essential to remember that it’s not a silver bullet.
Dr. Mark Thompson, a renowned automotive engineer, and author of “Securing the Connected Car: A Comprehensive Guide,” emphasizes this point:
“Relying solely on a single tool, however sophisticated, is akin to locking your front door but leaving all the windows open. A holistic approach encompassing robust security protocols, regular software updates, and driver awareness is crucial for a truly secure driving experience.”
Staying Ahead of the Curve
The automotive cybersecurity landscape is constantly evolving, with new threats emerging daily. As such, staying informed and adopting a proactive approach is paramount.
For further assistance in navigating this complex world and safeguarding your vehicle, feel free to reach out to our team of automotive experts via WhatsApp at +84767531508. We’re here to answer your questions and provide tailored solutions to meet your specific needs.
Drive with Confidence, Drive with Security
The digital age has brought about unprecedented advancements in the automotive industry, but it has also ushered in a new era of cyber threats. By understanding these threats and equipping ourselves with the right tools and knowledge, like the Crowdstrike scanning tool, we can mitigate risks and enjoy the open road with confidence and security.


