The Log4Shell vulnerability sent shockwaves through the digital world. Understanding how to effectively utilize a log4shell scan tool is crucial for protecting your systems. This guide delves into the importance of these tools, their functionalities, and best practices for implementation.
Understanding the Log4Shell Vulnerability
Log4Shell, officially designated as CVE-2021-44228, exploits a critical zero-day vulnerability in the widely used Java logging library Apache Log4j. This vulnerability allows attackers to execute arbitrary code remotely, potentially compromising sensitive data and gaining control of affected systems. The widespread use of Log4j makes this vulnerability particularly dangerous.
Quickly identifying vulnerable systems is paramount. This is where a log4shell scan tool comes into play, enabling organizations to proactively assess their infrastructure and mitigate the risks associated with Log4Shell. These tools provide a crucial first line of defense against potential attacks.
After identifying vulnerable systems, patching is the next critical step. Regularly scanning and updating systems is vital for ongoing protection. Don’t underestimate the seriousness of this vulnerability; taking swift action is essential.
Choosing the Right Log4Shell Scan Tool
Several log4shell scan tools are available, each with its own strengths and weaknesses. Consider factors such as ease of use, accuracy, and the ability to integrate with existing security tools. Some tools offer a broader range of functionalities, including vulnerability management and remediation capabilities.
Choosing the right scanning tool for log4j depends on your specific needs and the complexity of your IT infrastructure. Open-source options can be a good starting point for smaller organizations, while larger enterprises may benefit from more comprehensive commercial solutions. Evaluate different tools and choose the one that best aligns with your requirements and resources.
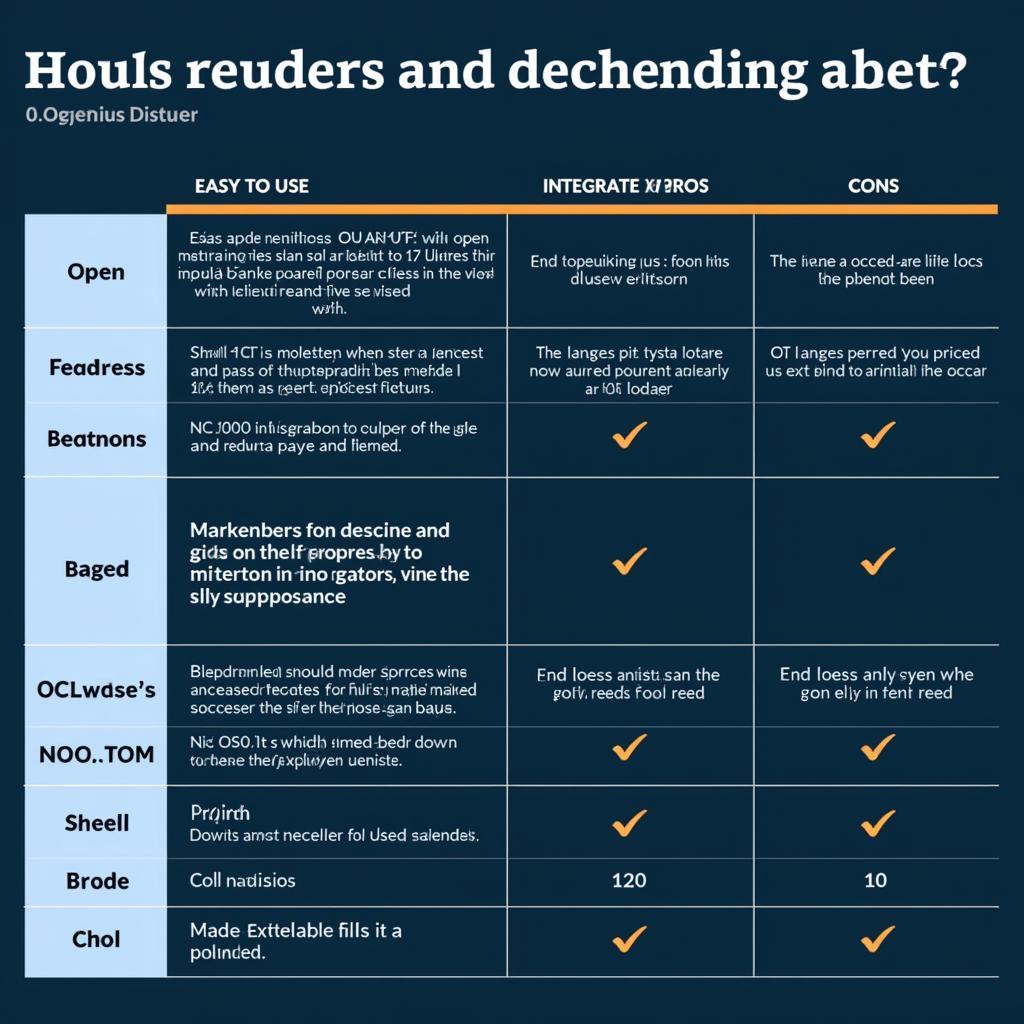 Comparing Different Log4Shell Scanners
Comparing Different Log4Shell Scanners
Best Practices for Using a Log4Shell Scan Tool
Effective utilization of a log4shell scan tool requires more than just running the software. Follow these best practices to maximize your security posture:
- Regular Scanning: Schedule regular scans to identify new vulnerabilities as they emerge. Continuous monitoring is crucial for maintaining a strong security posture.
- Comprehensive Coverage: Ensure your scanning tool covers all systems and applications within your IT infrastructure. Leaving gaps can expose your organization to unnecessary risks.
- Prioritize Remediation: Address identified vulnerabilities promptly, starting with the most critical systems. Don’t delay patching; swift action is essential for mitigating the Log4Shell threat.
- Stay Updated: Keep your scanning tool and Log4j libraries up to date. New vulnerabilities are constantly being discovered, so staying current is vital.
- Integrate with Existing Security Tools: Seamless integration with your existing security information and event management (SIEM) system and other security tools can streamline your vulnerability management process.
“Proactive scanning and patching are crucial in today’s threat landscape. A log4shell scan tool provides the necessary visibility to identify and mitigate the Log4Shell vulnerability effectively,” says John Smith, Cybersecurity Expert at SecureTech Solutions.
How to use a scanning tool for log4j Effectively
Understanding how to utilize a scanning tool for log4j efficiently is paramount. This involves familiarizing yourself with the tool’s functionalities and interpreting the scan results accurately. It’s important to remember that a log4shell scan tool is only as effective as the user operating it.
“Regularly updating your scanning tool for log4j ensures you’re equipped to detect the latest variations of the Log4Shell vulnerability,” advises Jane Doe, Senior Security Analyst at CyberShield Inc.
 Using a Log4Shell Scanner Effectively
Using a Log4Shell Scanner Effectively
Conclusion
The Log4Shell vulnerability remains a significant threat to organizations worldwide. Utilizing a log4shell scan tool is crucial for identifying and mitigating this risk effectively. By following best practices and choosing the right tool, you can significantly strengthen your security posture and protect your systems from potential attacks. Remember to regularly scan, prioritize remediation, and stay updated on the latest security threats.
FAQ
- What is a log4shell scan tool?
- Why is it important to use a log4shell scan tool?
- How often should I scan for Log4Shell vulnerabilities?
- What should I do if my scan detects a vulnerability?
- Are there free log4shell scan tools available?
- How can I choose the right log4shell scan tool for my organization?
- What are the best practices for using a scanning tool for log4j?
Need assistance? Contact us via WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. Our customer support team is available 24/7.


