Web application vulnerability scanning tools are essential for identifying security weaknesses in your web applications before they can be exploited by malicious actors. These automated tools help businesses protect sensitive data, maintain customer trust, and avoid costly data breaches. Finding the right tool for your specific needs can be challenging, so this guide will help you navigate the landscape and make informed decisions.
Ensuring web application security is no longer a luxury but a necessity. Cyberattacks are becoming increasingly sophisticated, and businesses of all sizes are vulnerable. Using a web application vulnerability scanning tool is a proactive approach to security that can save you time, money, and reputation. A robust web application vulnerability scanning tool is your first line of defense against cyber threats. Learn how to choose the best one for your organization’s needs.
What are Web Application Vulnerability Scanning Tools?
Web application vulnerability scanning tools are automated software solutions designed to identify security vulnerabilities within web applications. These tools work by simulating attacks on your web application, probing for weaknesses in the code, configuration, and other areas that could be exploited by hackers. They analyze a wide range of potential vulnerabilities, including cross-site scripting (XSS), SQL injection, cross-site request forgery (CSRF), and many more.
Imagine a security guard patrolling your web application, constantly looking for potential entry points for intruders. That’s essentially what a web application vulnerability scanning tool does. It acts as a virtual security expert, continuously monitoring your application for any signs of weakness. This automated process allows security teams to prioritize fixes and ensure the overall security posture of their web applications. The best web application vulnerability scanning tool will not only identify vulnerabilities but also offer practical remediation advice.
After this introduction, we will delve deeper into the types of web application vulnerability scanning tools available. Choosing the right tool is crucial for effective security management. For open-source options, check out our open source security scanning tools.
Types of Web Application Vulnerability Scanners
There are various types of web application vulnerability scanning tools, each with its strengths and weaknesses. Choosing the right one depends on your specific needs and resources.
Static Application Security Testing (SAST)
SAST tools analyze the source code of your application without actually running it. They are useful for finding vulnerabilities early in the development lifecycle. Think of it like proofreading a document before publishing it. SAST tools help identify potential errors and inconsistencies in the code itself.
Dynamic Application Security Testing (DAST)
DAST tools test the application in its running state, simulating real-world attacks to identify vulnerabilities. This is more like a penetration test, where the tool tries to actively exploit vulnerabilities. For information about network scanning tools, you can visit our page on network scanning & hacking tools.
Interactive Application Security Testing (IAST)
IAST combines elements of both SAST and DAST, offering more comprehensive coverage. IAST tools monitor the application from within during runtime, providing detailed insights into vulnerabilities and their potential impact.
Software Composition Analysis (SCA)
SCA tools analyze the open-source and third-party components used in your application to identify known vulnerabilities. Many applications rely on external libraries, and SCA helps ensure that these components are also secure. If you’re interested in tools for specific platforms like GitLab, see our page on gitlab security scanning tools.
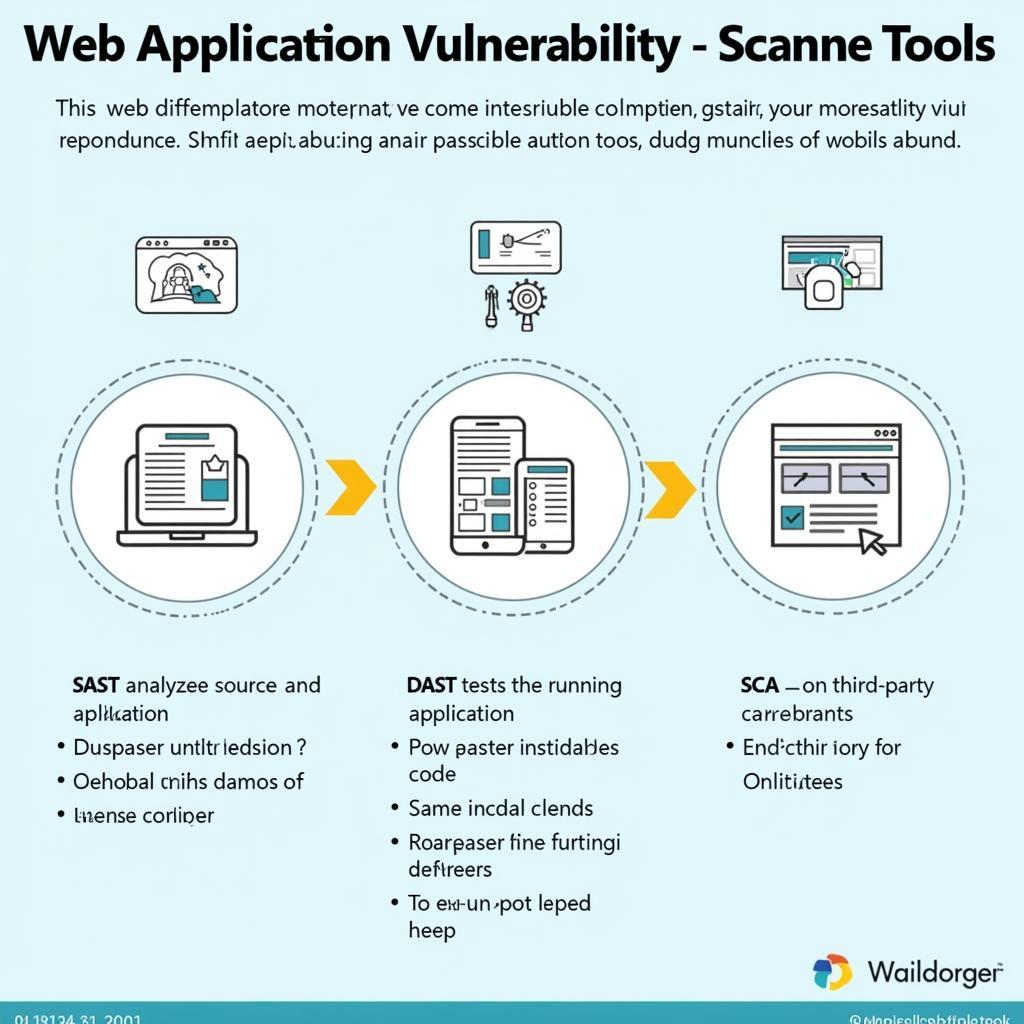 Web Application Vulnerability Scanning Tool Types: SAST, DAST, IAST, SCA
Web Application Vulnerability Scanning Tool Types: SAST, DAST, IAST, SCA
Why Use a Web Application Vulnerability Scanning Tool?
Implementing a web application vulnerability scanning tool is crucial for proactive security management. Here are some key benefits:
- Early Detection: Identify vulnerabilities early in the development lifecycle, reducing the cost and effort of fixing them later.
- Comprehensive Coverage: Scan for a wide range of vulnerabilities, ensuring comprehensive security coverage.
- Automated Testing: Automate the security testing process, saving time and resources.
- Compliance: Meet industry regulations and compliance requirements related to web application security.
- Enhanced Security Posture: Strengthen your overall security posture and reduce the risk of data breaches.
“A proactive approach to security is essential in today’s threat landscape,” says John Smith, Cybersecurity Expert at SecureTech Solutions. “Web application vulnerability scanning tools are indispensable for identifying and mitigating risks before they can be exploited.”
 Benefits of Using Web Application Vulnerability Scanning Tools: Early Detection, Comprehensive Coverage, Automated Testing, Compliance, Enhanced Security Posture
Benefits of Using Web Application Vulnerability Scanning Tools: Early Detection, Comprehensive Coverage, Automated Testing, Compliance, Enhanced Security Posture
How to Choose the Right Web Application Vulnerability Scanning Tool?
Choosing the right web application vulnerability scanning tool depends on several factors, including your budget, technical expertise, and specific security needs. Consider these aspects when making your decision:
- Type of Scanning: Decide which type of scanning (SAST, DAST, IAST, SCA) best suits your requirements.
- Ease of Use: Choose a tool that is easy to use and integrate into your existing workflow.
- Reporting and Analytics: Look for a tool that provides detailed reports and analytics to help you understand and prioritize vulnerabilities.
- Integration with Other Tools: Ensure the tool integrates seamlessly with your other security and development tools. If you’re interested in scheduling scans with audit tools, you can explore general audit tool schedule scans.
- Cost: Consider the cost of the tool and whether it fits within your budget. Explore options ranging from open-source solutions to commercial platforms.
“The right web application vulnerability scanning tool can be a game-changer for your organization’s security,” says Jane Doe, Security Consultant at CyberShield Inc. “It’s essential to choose a tool that aligns with your specific needs and resources.” If you are looking for specific scanning tools, consider our page on concrete scanning tools.
Conclusion
Web application vulnerability scanning tools are a critical component of any robust security strategy. By identifying and addressing vulnerabilities proactively, you can protect your organization from costly data breaches and maintain the trust of your customers. Choosing the right tool requires careful consideration of your specific needs and resources. Investing in a web application vulnerability scanning tool is an investment in the long-term security and success of your business.
FAQ
- What is the difference between SAST and DAST?
- How often should I scan my web applications?
- What are the most common web application vulnerabilities?
- How can I fix vulnerabilities found by a scanning tool?
- What is the cost of a web application vulnerability scanning tool?
- Is it necessary to use multiple types of scanning tools?
- How can I integrate a scanning tool into my development workflow?
Common Scenarios
- Scenario 1: A developer wants to integrate security testing into their CI/CD pipeline.
- Scenario 2: A security team needs to perform regular vulnerability assessments of their web applications.
- Scenario 3: A small business owner wants to ensure their website is secure from common attacks.
Further Exploration
- Explore our resources on web application security best practices.
- Learn more about different types of vulnerability scanning techniques.
Contact Us
For support, please contact us via WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. We have a 24/7 customer support team.


