Log4j vulnerabilities shook the cybersecurity world. Understanding how a log4j scan tool works and how to effectively use one is crucial for protecting your systems. This article dives deep into the world of log4j scanners, providing valuable insights for both individuals and businesses.
What is a Log4j Scan Tool?
A log4j scan tool is a software application designed to detect instances of the vulnerable Log4j library within your systems. These tools analyze files, network traffic, and other data sources to identify potential vulnerabilities. The goal is to find and mitigate the risk before malicious actors can exploit them. Choosing the right scanning tool for log4j is paramount to ensuring comprehensive coverage and effective remediation. You need a tool that not only identifies the vulnerability but also provides actionable insights for fixing it.
Many organizations were caught unprepared by the Log4j vulnerability. Don’t let that be you. A proactive approach to security, including the use of a reliable log4j scan tool, is the best defense. Staying ahead of the curve with regular scans can save your business from potentially catastrophic consequences. Utilizing a scanning tool for log4j can be a game-changer in your vulnerability management strategy.
 Log4j scan tool analyzing system files for vulnerabilities
Log4j scan tool analyzing system files for vulnerabilities
Why is Scanning for Log4j Vulnerabilities Important?
The Log4j vulnerabilities are particularly dangerous due to their widespread use and ease of exploitation. Attackers can gain remote code execution, allowing them to control affected systems. This can lead to data breaches, system disruption, and significant financial losses. Therefore, scanning for these vulnerabilities is not just a good practice, it’s a necessity. Regular scanning is crucial for maintaining a robust security posture.
How Does a Log4j Scan Tool Work?
Log4j scan tools utilize various techniques to detect vulnerabilities. Some common methods include:
- Signature-based scanning: Searching for specific patterns in files and network traffic that indicate the presence of the vulnerable Log4j library.
- Dependency analysis: Examining software dependencies to identify vulnerable versions of Log4j.
- Runtime analysis: Observing system behavior to detect exploitation attempts.
Choosing the right log4j2 scan tool will depend on your specific needs and environment.
How to Choose the Right Log4j Scan Tool
Selecting the right log4j scan tool can be overwhelming. Here are some key factors to consider:
- Accuracy: The tool should be able to accurately identify both known and emerging Log4j vulnerabilities.
- Ease of use: The tool should be easy to deploy and use, even for non-technical users.
- Comprehensive coverage: The tool should be able to scan a wide range of systems and applications.
- Actionable insights: The tool should provide clear and concise information about identified vulnerabilities, along with recommendations for remediation.
“A comprehensive scan tool log4j is essential for any organization utilizing Java-based applications,” says cybersecurity expert, Dr. Annabelle Lee, Ph.D. “The Log4j vulnerability highlighted the importance of proactive security measures and having the right tools in place.”
Integrating a Log4j Scan Tool into Your Security Strategy
Integrating a log4j scan tool into your existing security strategy is critical for ongoing protection. Regular scans should be scheduled and automated to ensure continuous monitoring. It’s also crucial to stay updated on the latest Log4j vulnerabilities and ensure your scan tool is configured to detect them.
Best Practices for Using a Log4j Scan Tool
- Regular scanning: Schedule regular scans to identify vulnerabilities promptly.
- Vulnerability management: Implement a process for managing and remediating identified vulnerabilities.
- Stay updated: Keep your scan tool and systems updated with the latest security patches.
- Comprehensive approach: Combine log4j scanning with other security measures for a layered defense.
“Don’t just scan once and forget about it,” advises John Miller, Senior Security Consultant at CyberSecure Solutions. “Regular scanning and proactive vulnerability management are crucial for minimizing your risk.”
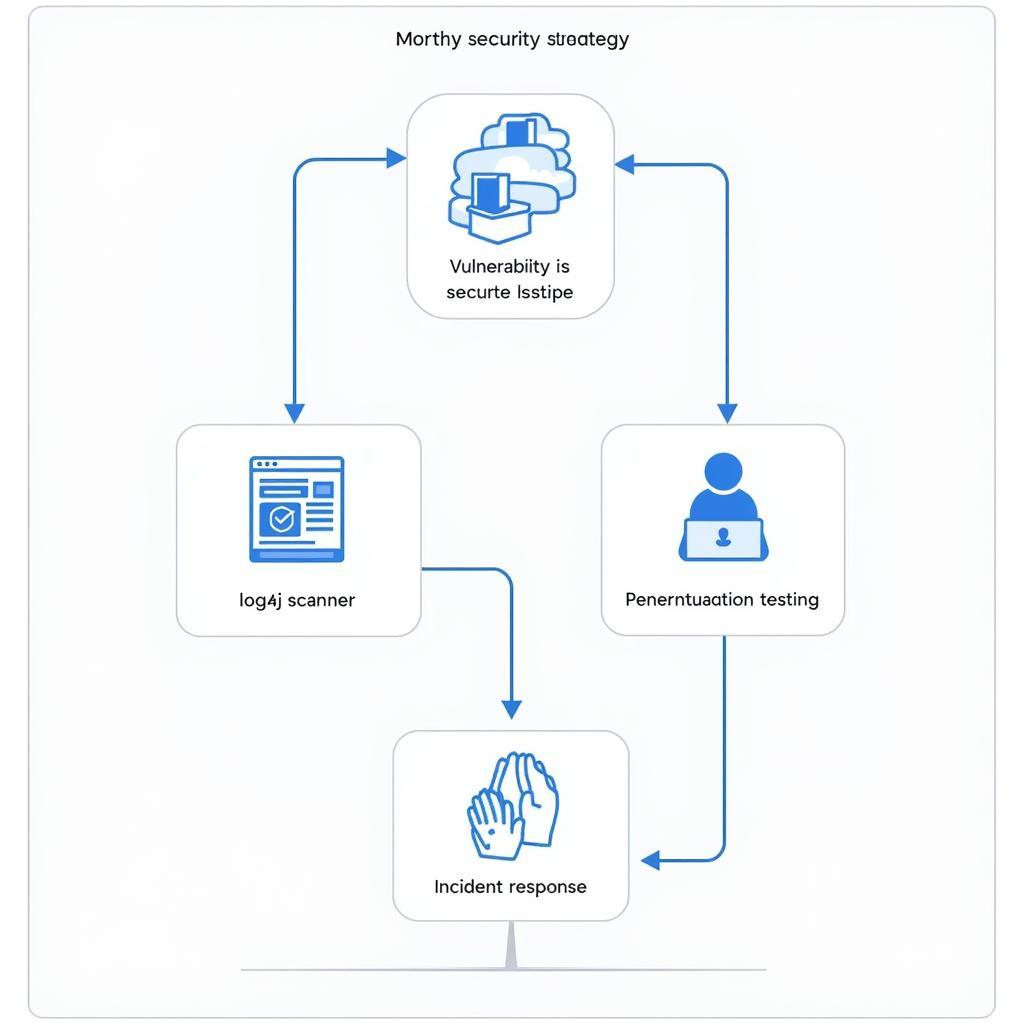 Diagram illustrating how to integrate a log4j scanner into a comprehensive security strategy
Diagram illustrating how to integrate a log4j scanner into a comprehensive security strategy
Conclusion
Protecting your systems from Log4j vulnerabilities requires a proactive approach. A log4j scan tool is an essential tool in your cybersecurity arsenal. By choosing the right tool and integrating it into your security strategy, you can effectively identify and mitigate these critical vulnerabilities, safeguarding your business from potential threats. Using reliable application vulnerability scan tools is crucial for a proactive security approach.
FAQ
- What is the best log4j scan tool? The best tool depends on your specific needs and environment. Consider factors like accuracy, ease of use, and comprehensive coverage.
- How often should I scan for Log4j vulnerabilities? Regular scanning, at least monthly, is recommended. More frequent scans may be necessary for high-risk environments.
- What should I do if a vulnerability is found? Immediately implement the recommended remediation steps provided by your log4j scan tool.
- Can a log4j scan tool prevent attacks? While it can’t prevent all attacks, it can significantly reduce your risk by identifying and helping you mitigate vulnerabilities before they are exploited.
- Are there free log4j scan tools available? Yes, some free tools are available, but they may not offer the same features and capabilities as commercial solutions.
- Do I need technical expertise to use a log4j scan tool? Some tools are designed for ease of use, even for non-technical users.
- How do I integrate a log4j scan tool into my existing security infrastructure? Most tools offer integration options with other security solutions.
Need support? Contact us via WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. We have a 24/7 customer support team.


