In today’s interconnected world, securing your software is paramount. Using effective tools to scan code for vulnerabilities is no longer a luxury but a necessity for every developer and organization. This guide explores the essential aspects of code scanning, helping you choose the right tools and strategies to protect your applications from potential threats.
Understanding the Importance of Code Scanning Tools
Software vulnerabilities are flaws in code that attackers can exploit to gain unauthorized access, steal data, or disrupt services. Identifying and fixing these vulnerabilities before they are exploited is crucial. This is where code scanning tools come into play. These tools automate the process of reviewing code for potential security risks, saving time and resources while enhancing the overall security posture. Early detection of vulnerabilities through code scanning significantly reduces the cost and effort associated with fixing them later in the development cycle. Choosing the appropriate scanning tools can be the difference between a secure application and a vulnerable one. Even seemingly minor vulnerabilities can have devastating consequences. Secure code is the foundation of a secure application.
You can find robust secure code scanning tools readily available in the market.
Types of Code Scanning Tools
There’s a wide range of code scanning tools available, each designed to address specific types of vulnerabilities and programming languages. Understanding these different types is key to selecting the right tools for your needs.
Static Application Security Testing (SAST)
SAST tools analyze source code without actually executing it. They examine the code’s structure, syntax, and data flow to identify potential vulnerabilities. SAST tools are effective in detecting a wide range of vulnerabilities, including buffer overflows, SQL injection, and cross-site scripting (XSS).
Dynamic Application Security Testing (DAST)
DAST tools analyze running applications to identify vulnerabilities. They simulate attacks and observe the application’s response to detect weaknesses. DAST is particularly effective in finding runtime vulnerabilities and issues related to authentication and authorization.
Software Composition Analysis (SCA)
SCA tools focus on identifying known vulnerabilities in third-party libraries and components used in your application. They compare the versions of libraries used in your project with vulnerability databases to detect potential risks.
“Regularly updating your libraries is crucial,” advises John Doe, Lead Security Engineer at SecureSoft Inc. “SCA tools help ensure you’re not using outdated components with known vulnerabilities.”
 Types of Code Scanning Tools
Types of Code Scanning Tools
Choosing the Right Tools to Scan Code for Vulnerabilities
Selecting the right tools depends on several factors, including your project’s specific requirements, programming languages, and budget. Consider these key aspects:
- Programming Language Support: Ensure the tool supports the languages used in your project.
- Integration with Development Workflow: Choose tools that integrate seamlessly with your existing development environment and CI/CD pipeline.
- Reporting and Remediation Guidance: Look for tools that provide clear and actionable reports, including detailed explanations of vulnerabilities and recommendations for fixing them.
- Scalability and Performance: Choose tools that can handle the size and complexity of your codebase without impacting performance.
Best Practices for Effective Code Scanning
Maximizing the effectiveness of your code scanning tools requires adopting best practices:
- Regular Scanning: Integrate code scanning into your CI/CD pipeline to ensure regular checks for vulnerabilities.
- False Positive Management: Develop a process for handling false positives to avoid wasting time on non-issues.
- Prioritize Remediation: Address critical vulnerabilities first based on their severity and potential impact.
- Stay Updated: Keep your scanning tools and vulnerability databases up-to-date to catch the latest threats.
“Don’t just scan for vulnerabilities, fix them,” says Jane Smith, Cybersecurity Consultant at CyberSecure Solutions. “A consistent remediation process is key to maintaining a secure application.”
You can find effective automated code scanning tools that seamlessly integrate into your development workflow.
Conclusion
Tools to scan code for vulnerabilities are indispensable for building secure software in today’s threat landscape. By understanding the different types of tools available, choosing the right tools for your needs, and following best practices, you can significantly enhance the security posture of your applications and protect your business from potential risks. Remember, continuous vigilance and proactive security measures are crucial in the ongoing battle against cyber threats.
FAQ
- What is the difference between SAST and DAST? SAST analyzes source code, while DAST analyzes running applications.
- Why is SCA important? SCA helps identify vulnerabilities in third-party libraries.
- How often should I scan my code? Ideally, code scanning should be integrated into your CI/CD pipeline for continuous monitoring.
- What is a false positive? A false positive is a reported vulnerability that isn’t actually a security risk.
- How can I prioritize vulnerability remediation? Focus on critical vulnerabilities with high severity and potential impact.
You may also want to explore resources on web server security scan tools for a more comprehensive approach to server security.
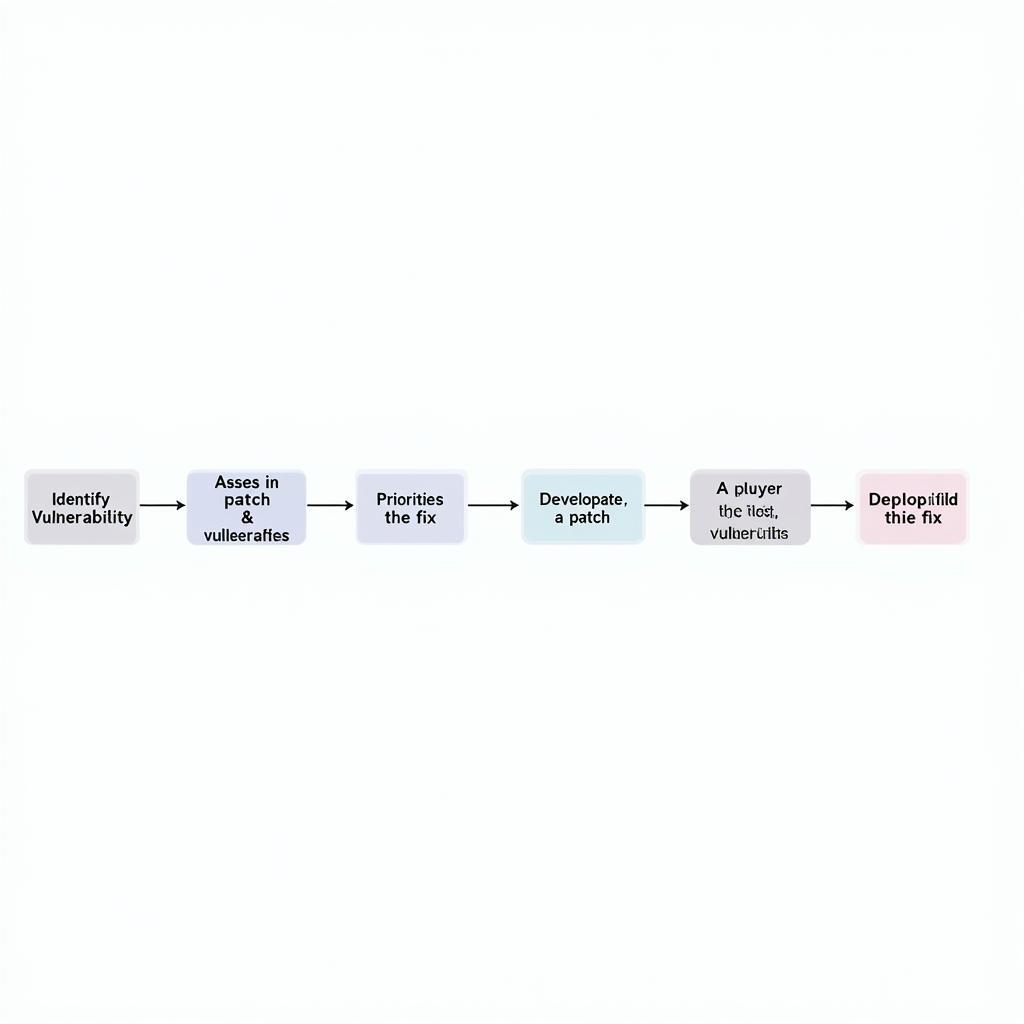 Vulnerability Remediation Process
Vulnerability Remediation Process
Have a look at our new server setup security scan tool guide and our resources on software tools for scanning for personal data to enhance your data privacy efforts.
For further insights, explore related articles on code analysis and security best practices within our website. Consider also our resources on secure coding practices and vulnerability management.
When you need assistance, please contact us via WhatsApp: +1(641)206-8880, Email: [email protected] or visit us at 276 Reock St, City of Orange, NJ 07050, United States. We have a 24/7 customer support team.


