Imagine cruising down the Autobahn in your sleek Audi A4, the German engineering humming beneath you. Suddenly, a warning light flashes on your dashboard – a network error in your car’s system. You pull over, heart sinking. You need a diagnostic tool, but not just any tool – you need one that can delve into the intricate network of your car’s computer system, much like how Linux network scanning tools can map out the entirety of a network.
Just as a mechanic uses a dealer scanner to pinpoint issues in your Audi’s intricate electrical system, network administrators and security professionals rely on Linux network scanning tools to gain a comprehensive understanding of their network infrastructure. These tools are crucial for maintaining network security, troubleshooting connectivity problems, and optimizing network performance.
Unveiling the Power of Linux Network Scanning Tools
In the realm of network management, visibility is key. You wouldn’t drive your Mercedes-Benz S-Class through the winding roads of the Swiss Alps without headlights, would you? Similarly, navigating the complexities of a network demands clear visibility into connected devices, open ports, and potential vulnerabilities. This is where Linux network scanning tools come into play.
These tools function as the “eyes and ears” of network administrators, providing them with critical insights to ensure smooth and secure operations. Just like how a mechanic uses an OBD-II scanner to diagnose engine problems in a Ford F-150, network professionals utilize these tools to:
- Identify active hosts on a network: Discovering all devices connected to the network, including servers, desktops, laptops, and even IoT devices.
- Pinpoint open ports and services: Determining which ports are open on a specific device and what services are running on those ports.
- Uncover vulnerabilities: Detecting potential security loopholes that malicious actors could exploit.
- Map network topology: Creating a visual representation of the network layout, showcasing the connections between different devices and subnets.
By providing these capabilities, Linux network scanning tools empower administrators to make informed decisions about network configuration, security policies, and resource allocation.
For a deeper dive into application security, check out our resources on Application Security Scanning Tools.
Nmap: The Swiss Army Knife of Network Scanning
When it comes to Linux network scanning tools, Nmap stands tall as a true icon. Just like a Bosch diagnostic tool is essential for any mechanic working on European cars, Nmap has become an indispensable asset for network professionals worldwide. Its versatility, combined with a robust feature set, has earned it the reputation of being the “Swiss Army Knife” of network scanning.
Nmap (Network Mapper) is a free and open-source utility renowned for its flexibility and power. It can be used for a wide range of network scanning tasks, including:
- Host discovery: Identifying active hosts on a network by sending out ICMP echo requests (ping) or TCP SYN packets.
- Port scanning: Determining which ports are open on a target host and what services are running on those ports.
- Operating system detection (OS fingerprinting): Identifying the operating system running on a remote device by analyzing its network responses.
- Version detection: Determining the version of services running on a host.
- Firewall evasion: Employing various techniques to bypass firewalls and intrusion detection systems.
 Nmap Command Line Interface
Nmap Command Line Interface
Let’s say you’re tasked with securing a network for a car dealership in California. Using Nmap, you can quickly identify all devices connected to the network, pinpoint open ports and services, and even detect potential vulnerabilities on devices like the credit card processing machine.
Beyond its core functionality, Nmap boasts a vibrant community and extensive documentation, making it an excellent choice for both beginners and seasoned professionals.
Beyond Nmap: Exploring Other Powerful Linux Network Scanning Tools
While Nmap reigns supreme in the network scanning landscape, a plethora of other powerful tools are at your disposal, each offering unique capabilities and catering to specific needs. These tools provide network administrators with a comprehensive arsenal to tackle various challenges:
- Zenmap: A graphical user interface for Nmap, simplifying network scanning tasks for those who prefer a visual approach.
- Masscan: Designed for lightning-fast scanning, Masscan excels at scanning large networks and internet ranges. It can scan the entire internet for specific open ports in just a matter of minutes.
- Unicornscan: Focuses on stealth and advanced techniques to evade intrusion detection systems, making it valuable for penetration testing and security audits.
- Angry IP Scanner: A cross-platform and user-friendly network scanner known for its speed and ease of use. It’s an excellent option for quickly identifying active hosts and open ports on a local network.
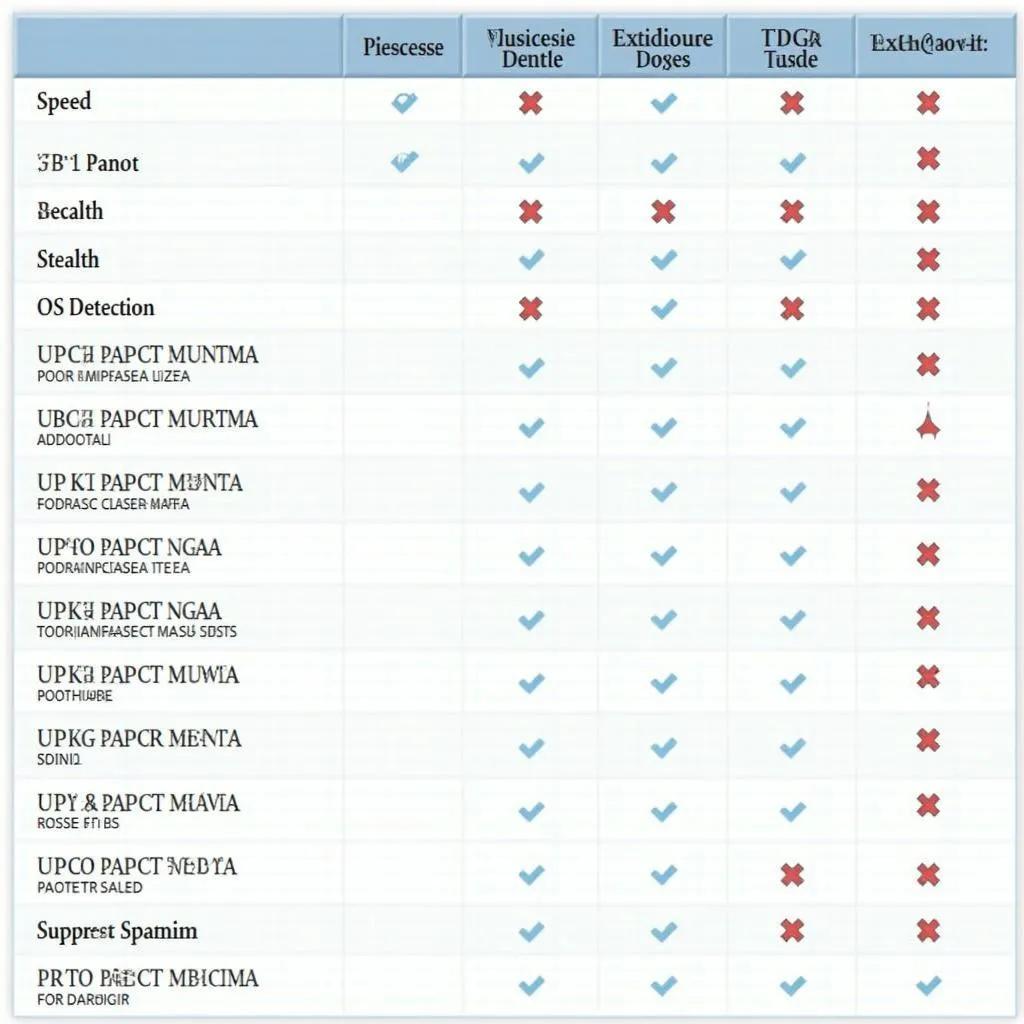 Network Scanning Tools Comparison Table
Network Scanning Tools Comparison Table
These tools, along with Nmap, form a formidable toolkit for any network professional. By understanding their strengths and weaknesses, you can choose the right tool for the job and ensure the security and efficiency of your network.
To learn more about network scanning tools specifically for Ubuntu, explore our dedicated resource: Network Scanning Tools Ubuntu.
Choosing the Right Tool for the Job
Selecting the appropriate Linux network scanning tool depends on the specific task at hand.
- For routine network checks and basic vulnerability assessments, Nmap’s versatility makes it an excellent choice.
- When speed is paramount, such as scanning large networks or internet ranges, Masscan reigns supreme.
- For security audits and penetration testing, Unicornscan’s stealth capabilities make it a valuable asset.
Understanding the strengths and weaknesses of each tool is crucial for making informed decisions about which one to use in different scenarios.
Network Scanning: A Vital Aspect of Network Security
Network scanning is not just a technical exercise; it’s a fundamental aspect of maintaining a secure and reliable network infrastructure. By regularly scanning your network, you can:
- Identify and mitigate vulnerabilities: Discovering and addressing security loopholes before malicious actors can exploit them.
- Detect unauthorized devices: Identifying any rogue devices that may have connected to the network without authorization.
- Ensure compliance: Meeting regulatory requirements, such as PCI DSS, by demonstrating regular network security assessments.
 Network Security Concept Image
Network Security Concept Image
Remember, a well-maintained network is a secure network. By integrating regular network scanning into your security practices, you can stay one step ahead of potential threats and maintain a robust security posture.
Need Help with Network Scanning?
Are you ready to gain deeper insights into your network’s health and security? Our team of automotive and network security experts is here to help! Contact us on WhatsApp at +84767531508 for assistance with setting up and utilizing the right network scanning tools for your needs. Let us help you drive your network security to the next level!


